Some odd files were seen being accessed on a server share. When it was investigated, the files didn’t exist on the server at all and apparently never had. Through more testing, it appeared the client was making these requests. I thought it was maybe AV or some other product, but after disabling everything, they were still occurring. Finally, I tried from a freshly built VM (I’ve also tried on existing VMs and on a physical machine, though not on a freshly installed physical machine). No matter where I tried these following steps from, I would see 100s of these requests to read files on the share. I’m wondering if anyone has seen this before, or knows what could be doing this. Details below.
Updated:
Several people on Twitter commented that this was part of Windows Application Compatibility. While I was looking through files trying to find which might contain these paths, Francisco Falcon provided the answer. The files are referenced in c:\windows\apppatch\sysmain.sdb, which is used by c:\windows\system32\apphelp.dll.
Essentially, Windows is trying to determine if this unknown setup.exe (or install.exe or update.exe or …) need to be run with any compatibility mode options based on what it knows in the Application Compatibility Database. I know about Application Compatibility, but didn’t know it would be so proactive. Here are a few more links people provided with some additional information that may be helpful.
- http://www.alex-ionescu.com/?p=39
- http://www.alex-ionescu.com/?p=40
- https://msdn.microsoft.com/en-us/library/bb432182%28v=vs.85%29.aspx
- https://superuser.com/questions/857616/how-to-disable-installer-detection-feature-of-uac-in-windows-7-home-premium
I also modified the post below to add the files that are accessed when you encounter an install.exe or update.exe in case someone runs across this in the future and is searching for these filenames.
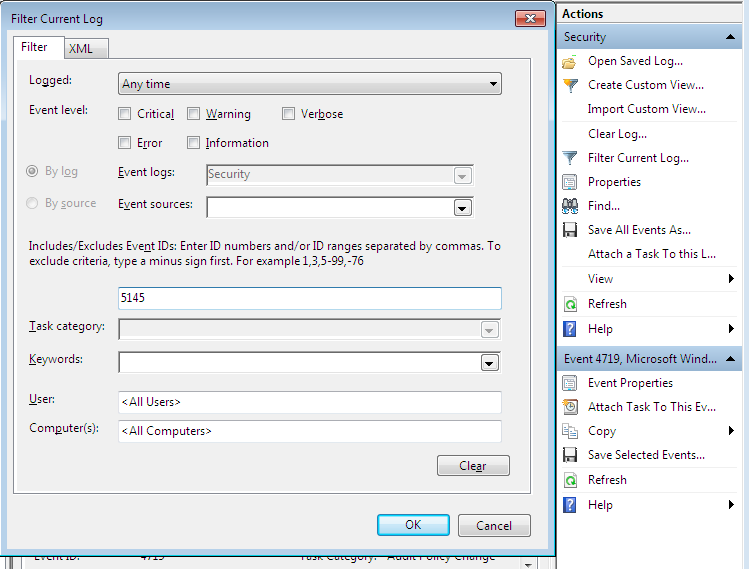
First, enable Detailed File Share Auditing. Execute the following commands from an elevated Administrator command prompt.
auditpol /set /subcategory:"Detailed File Share" /success:enable auditpol /set /subcategory:"Detailed File Share" /failure:enable
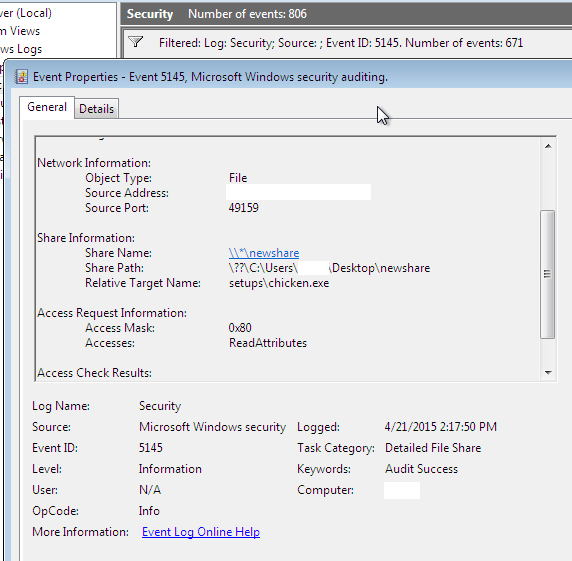
This will create events with an ID 5145 when files are accessed on the share. Next, open Event Viewer, open the Security Event log, and create an event ID filter on that number. Then, clear the log if you want to make it easier to only see new events.
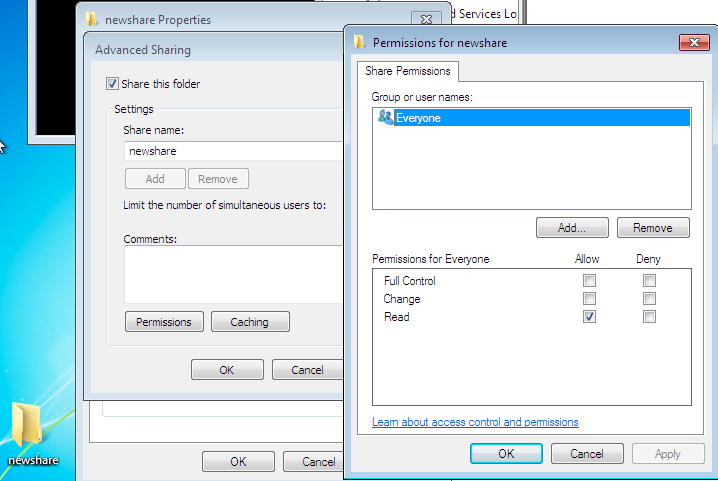
Next, open Explorer and either find a directory with no or few files in it or create a new one. It can have more files in it, but that will create more events and make it harder to find the odd requests. Then, share the folder out.
Create a file in that directory and name it anything, for example, test.txt.
Now, open a second Explorer window and browse to the share by going to:
\\<COMPUTERNAME>\<SHARENAME>
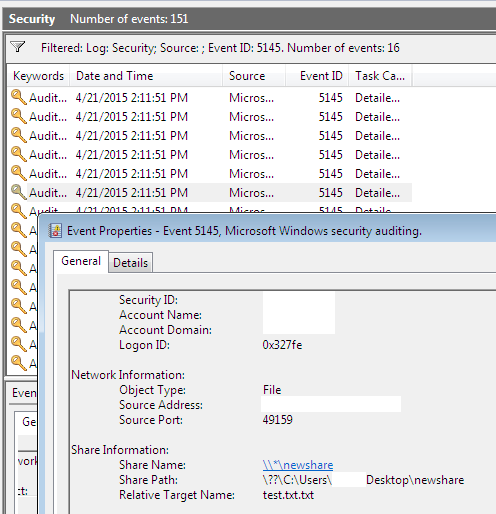
If you go back to Event Viewer and refresh, there should be about 15 or so events, depending on how many files are in the share.
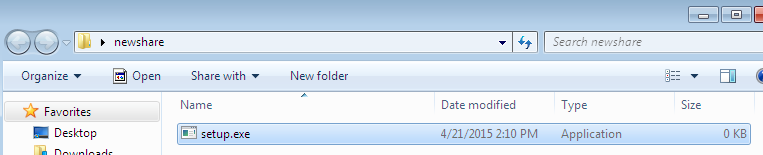
Now, go back to the Explorer window that has the directory on the filesystem open, not the one accessing the share. Rename the test file to setup.exe. Make sure Explorer is not setup to hide extensions. The icon for setup.exe should be the application icon, not the text document icon, and the Type should be Application as well.
Now, go back to the Explorer window accessing the share and refresh. Finally, go back to Event Viewer and hit Refresh there as well. In my testing, this will generate around 500+ events.
These are all read requests on files that don’t exist. I’ve also run PCAP on the machine and see the SMB CreateRequest with Read attributes set being sent out. AV logs from other testing indicated it was explorer.exe making the requests.
The question is why does Explorer try accessing all these files that don’t exist when it finds a “setup.exe” file in a directory? There could be other filenames that trigger this behavior, but so far I’ve only seen it for setup.exe. It also originally was detected with actual setup.exe files, so this isn’t some artifact of a 0-byte setup.exe. I also tried enabling File System auditing and Object Access. I think I enabled all the logging I would’ve needed, but didn’t see these request when accessing a directory containing “setup.exe” on the filesystem. It only seems to happen on a share.
Below is a full list of the files accessed in the 5145 events when encountering setup.exe, install.exe, and update.exe. In each case, the only targets that actually existed are the specific file mentioned, the base path of the share ‘\’, and desktop.ini.
Setup.exe – 290 files
Relative Target Name: 300\INSTALL\AVWSNTEA.EXE Relative Target Name: 301\INSTALL\AVWSNTJA.EXE Relative Target Name: 3rdPartyApp\GoogleToolBar\GoogleToolbarInstaller_zh-TW.exe Relative Target Name: ABBYY Lingvo 11\LvInstall.exe Relative Target Name: AOLTECH\MODEMS.SIM Relative Target Name: ActiveKnowledge modules\NetIQ Operations Manager and Security Manager.AKM Relative Target Name: Alpha Build 1272a\old\Vtest60.dll\VTest60.dll Relative Target Name: AppInst\quickcam.ico Relative Target Name: Attune\Bin\Attune.exe Relative Target Name: AutoRun\AutoRunI.exe Relative Target Name: BIN\dbutil.exe Relative Target Name: BIN\rsl.dll Relative Target Name: BKOFFICE\I386\MSOADMIN.EXE Relative Target Name: BOCLIENT\SETUP.EXE Relative Target Name: BOOTME\BOOTME.EXE Relative Target Name: Backup\File Backup.exe Relative Target Name: Backup\Premium Plus.exe Relative Target Name: Benchmgr\SERGT.exe Relative Target Name: Bin\Anno1701AddOn.exe Relative Target Name: Bin\DMoMM.dbd Relative Target Name: Bin\InocIT_NT_Client\inoculan.icf Relative Target Name: CDCREATR\CREATR32.EXE Relative Target Name: CDDATA\AUDIO\DEER000.WAV Relative Target Name: CD\XSERVER LIB Relative Target Name: CEPB\BIN\cemgr.exe Relative Target Name: CLIENT\VINTDEV\BIN\HTMSW.DLL Relative Target Name: COMANDOS\VIDEO\H_Afri.avi Relative Target Name: Common\Data\BGH4ItemList.csv Relative Target Name: Common\Dynamics NAV\Application Handler\NSAppHandler.dll Relative Target Name: Config\APP\DSLAPI32.INI Relative Target Name: Config\app\TangoManager.exe Relative Target Name: Cover\softPK_coverpage.css Relative Target Name: Custom\Custom_cowboy.psd Relative Target Name: DATA\Charlie.exe Relative Target Name: DATA\FOOD6.CXT Relative Target Name: DATA\MENU1.DAH Relative Target Name: DATA\MENU1.DAP Relative Target Name: DATA\MENU6.DAL Relative Target Name: DATA\ZOO.EXE Relative Target Name: DISK01NT\REACHOUT.PRM Relative Target Name: DISK1\REACHOUT.1 Relative Target Name: DISK2\PEDATA.Z Relative Target Name: DRIVER VALIDATION\DRIVERVALIDATION.EXE Relative Target Name: DRV\VSAPINT.SYS Relative Target Name: DXGUARD\DXG32.DLL Relative Target Name: Data\All\EBRide.exe Relative Target Name: Diagnostics\LANGMasterDoctor.exe Relative Target Name: Docs\PFM Workstation Install.doc Relative Target Name: Documentation\PFSv401.pdf Relative Target Name: Documentation\PN6ReadMe.doc Relative Target Name: Documentation\dnmu.pdf Relative Target Name: Dragon\DNSCompatibility.exe Relative Target Name: Drivers\Bin\CamWizard.exe Relative Target Name: Drivers\DualA.vxd Relative Target Name: Drivers\NT4Drv\MSI8042.sys Relative Target Name: Drivers\WinNTDrv\MSI8042.sys Relative Target Name: DsWin\DsWin.exe Relative Target Name: ED1_WIN\ED1_WIN.EXE Relative Target Name: EE\ENCARTA\ENC2001.EXE Relative Target Name: ESAS\esassetup.exe Relative Target Name: EXE\CFS3.EXE Relative Target Name: English\Dual-option_UserManual.pdf Relative Target Name: Engsetup\engsetup.exe Relative Target Name: External\JP\SD-JukeboxV6.pdf Relative Target Name: FILES\AD10th\TOASTERS.AD Relative Target Name: FISHIN\FISHIN.EXE Relative Target Name: Files\DSLOA.exe Relative Target Name: Files\Midas.exe Relative Target Name: Files\ShowCpyr\Version.dll Relative Target Name: Files\zt.exe Relative Target Name: Firewall\FwInstall.exe Relative Target Name: Firewall\TVdriverSetup.exe Relative Target Name: Fonts\data1.hdr Relative Target Name: GAME\DAYTONA USA Evolution.exe Relative Target Name: GAME\DRIVERDB.BIN Relative Target Name: GAME\LBWIN.EXE Relative Target Name: GUARDDOG\SETUP.EXE Relative Target Name: Game\lilopc.exe Relative Target Name: Game\wws98.exe Relative Target Name: Ground Control\GRAPHICS.SDF Relative Target Name: HELP\BB2001.HLP Relative Target Name: HELP\GOLFHELP.EXE Relative Target Name: HELP\NN5QSG.PDF Relative Target Name: Hallmark Card Studio 2005\Program Files\Sierra\Hallmark Card Studio 2005\Hallmark Card Studio.exe Relative Target Name: Handbuch\AVK InternetSecurity 2006.pdf Relative Target Name: I386\WSPCPL32.CPL Relative Target Name: I386\mspsec.dll Relative Target Name: IGD\IGD.msi Relative Target Name: INSTALLS\UTILITY\DiskGen.exe Relative Target Name: INSTALLS\pcAnywhere\Pca32\CD\Disk1\iscustom.dll Relative Target Name: INSTALL\Data\Sdreadme.pdf Relative Target Name: INSTALL\MGXFMA.Z Relative Target Name: INSTALL\emergy.exe Relative Target Name: IPfilter\ipfilter.sys Relative Target Name: Install\Data\All\XMntBike.exe Relative Target Name: Install\data\bzhw8.zfs Relative Target Name: Install\xtrmbnb.ico Relative Target Name: InstantCDDVD\InstantCDDVD.exe Relative Target Name: IntelNT\ARCserve.IT\ASCORE.DLL Relative Target Name: Intel\Setup.exe Relative Target Name: KPINSTALL\KpInstall\KPD3.exe Relative Target Name: LLW32\LLW.1 Relative Target Name: LLW32\LLWSETUP.INI Relative Target Name: Locale\English\TakeTwo.hlp Relative Target Name: MANUALS\2000TBOX\2000.PDF Relative Target Name: MANUALS\FI2000.PDF Relative Target Name: MANUALS\UI\UI_51.PDF Relative Target Name: MANUALS\Uninstal\UI_51.PDF Relative Target Name: MANUAL\EASYUN~1.PDF Relative Target Name: MANUAL\MAX2MAN.PDF Relative Target Name: MANUAL\WinTVMan_eng.EXE Relative Target Name: MDAC\2.51.5303.5\mdac_typ.exe Relative Target Name: MGRS\OVNEF.EXE Relative Target Name: MSBRAIN\MSBRAIN.EX_ Relative Target Name: MSN\msncore.exe Relative Target Name: MShow\Doc\Jpn\MediaShow_UG.pdf Relative Target Name: MYDVD_613\MyDVD.MSI Relative Target Name: ManagementStation\MgmtSt.msi Relative Target Name: Manual\Peachtree Office Accounting User's Guide.pdf Relative Target Name: Manuals\WebScanX.PDF Relative Target Name: Min\Asteroids.exe Relative Target Name: MsFteWds Relative Target Name: Mssdetect\iis_srv.inf Relative Target Name: MyCheckBook\Mysoft.ini Relative Target Name: NBA98\B0_00.VCT Relative Target Name: NRC\WINDOWS\INSTALL\EN\MAKEDISK.EXE Relative Target Name: NeroMix\API\WNASPI32.DLL Relative Target Name: NeroVision\NeroFiles\WNASPI32.DLL Relative Target Name: Newsflash\Newsflsh.exe Relative Target Name: Norman\NPF142R3_ENG.EXE Relative Target Name: OEM_\Plug-Ins\InCopyWorkflow\InCopyImport.apln Relative Target Name: OHELP60\BWCC.CNT Relative Target Name: Objects\boats\boat11.3df Relative Target Name: Oc\DATA.TAG Relative Target Name: Oil Change\readme.txt Relative Target Name: PIF\PIC\PIC_ENG.dll Relative Target Name: PIP2001\Pip.exe Relative Target Name: PIPOMATE\pipoma.exe Relative Target Name: PMap40\PMAP.BMP Relative Target Name: POWERBUILDER7\SETUP.INI Relative Target Name: PROGRAMS\PWFAXMGR.EXE Relative Target Name: Pack\CSI4_Optional_Install\CSI4_Movies_B\CSI4_Intro.bik Relative Target Name: Packager\Symantec Packager.msi Relative Target Name: Packages\Symantec pcAnywhere - AutoStart Host.msi Relative Target Name: Packages\Symantec pcAnywhere - AutoStart-Host.msi Relative Target Name: Press\PC6_manual partitioning.pcx Relative Target Name: Pro99\Seahawks.zip Relative Target Name: Pvr\pvr45xxx.EXE Relative Target Name: QCDriver\qcinsenu.dll Relative Target Name: QUICKEN\CUSTOM\QUICKOFF.INI Relative Target Name: QuickBooks Letters\Employee Letters\Sick time.doc Relative Target Name: QuickCam\QuickCam.exe Relative Target Name: QuickCam\Temp\LVIHlp.dll Relative Target Name: QuickCam\camware.exe Relative Target Name: ROLLOUT\AVSERVER\LDVPDIST.dll Relative Target Name: RTL8187B\VistaX86\rtl8187B.sys Relative Target Name: RUNIMAGE\DELPHI40\BIN\DFOLDER.DLL Relative Target Name: Redistrib\AdvSecMig\Migration\CFML.EXE Relative Target Name: Resources\MYOBODBC\ikernel.ex_ Relative Target Name: Response\clientCustom.rsp Relative Target Name: Roboword\Roboword.exe Relative Target Name: Rt_tts\spchapi.exe Relative Target Name: SEP\smcinst.exe Relative Target Name: SERVER\SQL RVSP\SETUP.EXE Relative Target Name: SETUP\Program\Msh_zwf.dll Relative Target Name: SETUP\VDB\SETUP.EXE Relative Target Name: SETUP\data1.cab Relative Target Name: SETUP\speedkey.exe Relative Target Name: SEVINST\SEVINST.EXE Relative Target Name: SOUNDS\SOUNDS.CC2 Relative Target Name: Samples\Internat SigmaPlot Macro Library.jnb Relative Target Name: Scenarios\Six Flags Magic Mountain.SC6 Relative Target Name: ServerControl\SCSetup.exe Relative Target Name: Setup\Creating Keepsakes Scrapbook Designer.msi Relative Target Name: Setup\Dino\HD\Dino.exe Relative Target Name: Setup\Princess Fashion\CD\bucket.cur Relative Target Name: Setup\PrintMaster 16.pdf Relative Target Name: Setup\The Print Shop 20.msi Relative Target Name: Setup\The Print Shop 22.msi Relative Target Name: Setup\hot2000\data\game\beachhi.plz Relative Target Name: Setup\videoc.dll Relative Target Name: Setup\win_vista\KT_WCM_KWD_U1300_200107038_VISTA.exe Relative Target Name: SharePoint Portal Server\Bin\MoveSPSDMFiles.exe Relative Target Name: Snova95\core\SNOVA95.EXE Relative Target Name: SnovaNT\core\SNOVANT.EXE Relative Target Name: SnovaNT\core\dolntdrv.dll Relative Target Name: Snova\core\Snova.EXE Relative Target Name: SoftICE\WinNT\Setup.Z Relative Target Name: Support\Images\Kef4.ico Relative Target Name: TEMPWE\WINEYES.EXE Relative Target Name: TMPWEPRO\GWM32.EXE Relative Target Name: TSINST\README.TS Relative Target Name: Textures\R-Luna.utx Relative Target Name: Tools\Automatic Install Image\BViewer.enu Relative Target Name: Tools\makedisk.exe Relative Target Name: Tracks\Batflyer.TD4 Relative Target Name: TurboTax 2008\TurboTax 2008 Installer.exe Relative Target Name: UTILITY\PartInNT.exe Relative Target Name: VCAFE\VCafe.ini Relative Target Name: VI1.0\CLIENT\IE30\MSIE301.EXE Relative Target Name: VISTSCAN\ENGLISH\DISK1\VSTA32.D_ Relative Target Name: VSC\WINXP\NAIFILTR.SYS Relative Target Name: VSP\WINXP\NAIFILTR.SYS Relative Target Name: Vista\Setup.exe Relative Target Name: WP4INET\HELP\ABOUT.HTM Relative Target Name: WW2001\WWSETUP.EXE Relative Target Name: Waves\WAVETAB.CFG Relative Target Name: What's_New_in_HomeSite_45\WhatsNewHS45.exe Relative Target Name: Win2000\Setup.exe Relative Target Name: ZX7SETUP\RELNOTES.TXT Relative Target Name: \ Relative Target Name: _AUTORUN\support\support.exe Relative Target Name: _autorun\SU.ico Relative Target Name: _autorun\autorun.exe Relative Target Name: _setup\HH2003.exe Relative Target Name: _setup\HH2004.exe Relative Target Name: a5w\a5j.exe Relative Target Name: american\AMERICAN.TXT Relative Target Name: anim\bullAKD\PBRBullA.vol Relative Target Name: av\setup.exe Relative Target Name: avi\eu2_intro.bik Relative Target Name: bkoffice\I386\bosres.dll Relative Target Name: camware\camware.exe Relative Target Name: core\def\wcescomm.exe Relative Target Name: corel\programs\wpwin9.exe Relative Target Name: d6run\ballbmo.bmp Relative Target Name: data\Data\Bikes.dat Relative Target Name: data\GSNA29.ico Relative Target Name: data\Heavy Gear 2.exe Relative Target Name: data\SOFTBALL.EXE Relative Target Name: data\TEACHER.EXE Relative Target Name: data\WP5.EXE Relative Target Name: data\arena1.atd Relative Target Name: data\ctp.ico Relative Target Name: data\pb2x.exe Relative Target Name: desktop.ini Relative Target Name: doc\images\9i_Internet_Logo.gif Relative Target Name: docs\AOEIIIStandard_Manual_JP.pdf Relative Target Name: docs\ss_security_aasg.htm Relative Target Name: documentation\AppManager Response Time\AM_AD-RT.pdf Relative Target Name: dvc325\data.tag Relative Target Name: ed5_win\ED5_WIN.EXE Relative Target Name: english\win95\OEMUSB.exe Relative Target Name: exchange\adc.exe Relative Target Name: fs98\fltsim95.exe Relative Target Name: ghostpe\Ghost\ghostpe.exe Relative Target Name: global\shared\osrv.msi Relative Target Name: global\wss.msi Relative Target Name: i386\_setup.exe Relative Target Name: ico\armada.ico Relative Target Name: installs\Phon\Phonetik.msi Relative Target Name: langs\ZTRes.dll Relative Target Name: lotus\approach\approach.exe Relative Target Name: mpfPlush\mpfPlusSetup.exe Relative Target Name: outloud\ttsclean.exe Relative Target Name: pcANY32\DISK1\SIWPCA.DLL Relative Target Name: pc\ammo\GRENADE\ammo.qvm Relative Target Name: peachw\PEACH.ICO Relative Target Name: program files\Clarify\clarify.exe Relative Target Name: program files\Kaspersky Lab\Kaspersky Anti-Virus for Workstation 5\FSSync.dll Relative Target Name: program files\Logitech\QuickCam\QuickCam.exe Relative Target Name: program files\MMIS\ASAdmin.dll Relative Target Name: program files\Microsoft BizTalk Server\Setup\BTSsetupDB.exe Relative Target Name: runtime\runtime.exe Relative Target Name: sdoe\SDemons.exe Relative Target Name: setup.exe Relative Target Name: setup\hpphotosmartessential\HPPhotosmartEssential.cab Relative Target Name: setup\i386\msetup.exe Relative Target Name: setup\mny6stp.dll Relative Target Name: setup\software\AIO_CDB_Software.msi Relative Target Name: setup\software_min\PS_AIO_02_Software_min.cab Relative Target Name: setup\software_min\PS_AIO_04_C6300_Software_Min.cab Relative Target Name: setups\chicken.exe Relative Target Name: sharedNT\incdrec.sys Relative Target Name: smoney50\MONEY.INI Relative Target Name: sounds\M03\MO3CO002.ACM Relative Target Name: sps\SPS.msi Relative Target Name: support\dotnetfx\dotnetfx.exe Relative Target Name: test.txt.txt Relative Target Name: tools\msoschma.exe Relative Target Name: ui\SwDRM.dll Relative Target Name: uninstall\istgun.exe Relative Target Name: win95\CxCap.DRV Relative Target Name: win98\w98setup.bin Relative Target Name: win98n\w98setup.bin Relative Target Name: wineyes\tmpwepro\wineyes.exe Relative Target Name: x86\BINN\dtspkg.dll Relative Target Name: x86\BINN\sqlservr.exe Relative Target Name: x86\setup\sql_rs.msi Relative Target Name: x86\x86\BINN\dtspkg.dll
Install.exe – 25 files
Relative Target Name: DATA\DISK\LEGOISLE.EXE Relative Target Name: DISK2\DATA2.CAB Relative Target Name: INSTALL\DATA.TAG Relative Target Name: INSTALL\SHGM.INF Relative Target Name: Inspiration Documentation\Getting Started.pdf Relative Target Name: InstallerData\Installer.zip Relative Target Name: QW_WIN95\SETUP.PKG Relative Target Name: RUNIMAGE\DELPHI40\BIN\DFWEDIT.DLL Relative Target Name: Runimage\delphi50\bin\coride50.bpl Relative Target Name: SETUP\ANTIVIR\ENU\SERVER\WINNT\SETUPEX.EXE Relative Target Name: SMARTCTR\SUITEST.EXE Relative Target Name: StoneAge\StoneAge.exe Relative Target Name: TRIAL\ANTIVIR\ENU\WORKSTAT\WINNT\FSAVNTWS.EXE Relative Target Name: WINNT\WMSSET.INF Relative Target Name: \ Relative Target Name: exe\org6.exe Relative Target Name: help\bcd\win\2003-dlx.chm Relative Target Name: install.exe Relative Target Name: jdk\java\jre\bin\java.exe Relative Target Name: lotus\approach\approach.exe Relative Target Name: setup\images\jbuilder.ico Relative Target Name: ui\SwDRM.dll Relative Target Name: win\setup\iPlayer.ico Relative Target Name: x64\System64\PDBoot.exe Relative Target Name: x86\System32\PDBoot.exe
Update.exe – 4 files
Relative Target Name: \ Relative Target Name: exchange\adc.exe Relative Target Name: ui\SwDRM.dll Relative Target Name: update.exe
Thanks so much for writing this! We noticed some endpoints doing some weird queries on one of our IIS servers. We were concerned that it might have been malware but your article helped me find the culprit and reassure management. Keep up the great work!
Glad to hear! It seemed like an odd problem at the time and hard to find info about it, so I hoped others would find it useful in the future.
Thank you very much. You are awesome. Our SOC raised alarm over suspicious file activity. After hours of analysis I googled some of the file names and ended up on your blog that clarified the issue. BR