In July, SANS announced the 2014 SANS Brochure Challenge. Over the course of 4 SANS event brochures, there would be hidden messages and codes and solving each one would lead to a series of other challenges. I spent a couple hours on them and was able to work my way through everything. It was a fun challenge and there were a few interesting elements (see the QR code embedded in an audio file). Here’s my write up.
There were 4 brochures shipped in July and August that were the starting points for each of the challenges. The name will take you to my write up for that brochure and the link goes to the PDF of the brochure. The Network Security brochure has the full introduction to the challenge, but the first piece of the challenge is really in the Albuquerque challenge, so I’ll start there.
- SANS Albuquerque – https://www.sans.org/event-downloads/34885/brochure.pdf
- SANS Baltimore – https://www.sans.org//event-downloads/32755/brochure.pdf
- SANS Seattle – https://www.sans.org//event-downloads/36155/brochure.pdf
- SANS Network Security – https://www.sans.org/event-downloads/35227/brochure.pdf
- Putting It All Together
SANS Albuquerque
Page 6 of the PDF (page 4 on the brochure) has a small banner on the left side with the following text:
The equals signs are usually a giveaway for Base64 encoding, and sure enough we can decode this.
$ echo aHR0cDovL2JpdC5seS8xbHA5MEx6Cg== | base64 -D http://bit.ly/1lp90Lz
This link redirects to http://brochure2014.counterhack.com/Challenge-1-Level-1-2F381761-B9C1-424F-AD21-51C19E1D5688/.
This page has the following text:
Great work! You are a master of MIME encodings.
The challenge is just starting, though, and resistance is futile. You’ll need to prove your assimilation of knowledge before you can proceed.
Which three annual SANS conferences have the most classes being taught? Remove the year and spaces from the conference titles, order the conferences from east to west, then add the three conferences to the end of http://bit.ly/SANS_ to generate the next URL. The answer is the same whether you search for training globally or just in North America.
For example, if the three conferences were SANS Rocky Mountain 2014, SANS Security West 2014, and SANS Virginia Beach 2014, the correct URL would be http://bit.ly/SANS_SANSVirginiaBeachSANSRockyMountainSANSSecurityWest.
The list of SANS conferences is at https://www.sans.org/security-training/by-location/north-america. By looking at the number of classes at each event, we can put together the list. The conferences are SANS FIRE, SANS (in Orlando), and SANS Network Security, which gives the link http://bit.ly/SANS_SANSFIRESANSSANSNetworkSecurity which redirects to http://brochure2014.counterhack.com/Challenge-1-Level-2-A6C853E7-945C-4DEF-ADAD-B1F0D8D619CC/.
This page has the following text:
Fascinating. You have an efficient intellect.
You’ve proven your knowledge of SANS lore. You have a continuing mission, though – starting with the below question.
Alice has sent Bob an encrypted file. Find it, decrypt it, and follow the URL inside.
The file at the link is a PCAP file.
Opening the file in Wireshark, there are a few interesting streams:
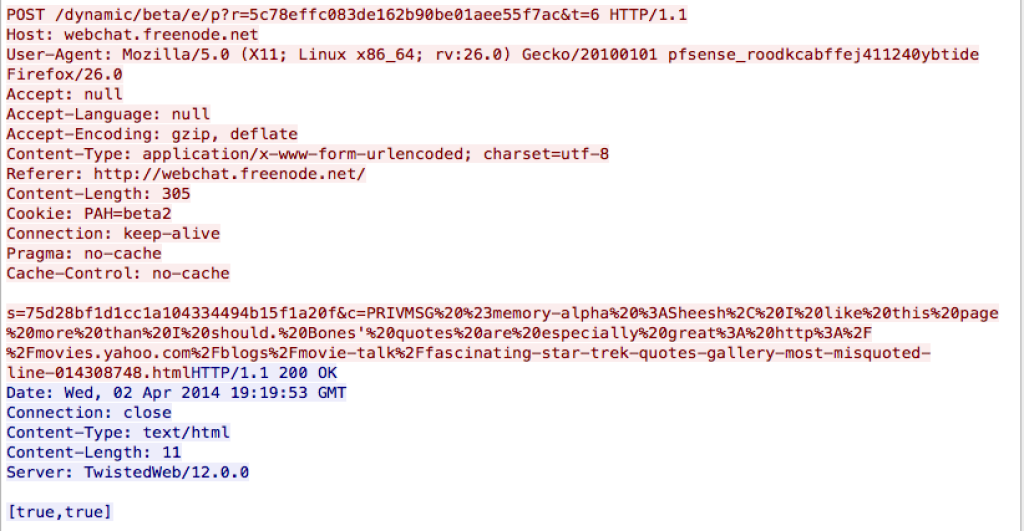
Applying a filter of “tcp.stream eq 20” contains the following in a POST request:
Take the content of the POST
s=75d28bf1d1cc1a104334494b15f1a20f&c=PRIVMSG%20%23memory-alpha%20%3ASheesh%2C%20I%20like%20this%20page%20more%20than%20I%20should.%20Bones’%20quotes%20are%20especially%20great%3A%20http%3A%2F%2Fmovies.yahoo.com%2Fblogs%2Fmovie-talk%2Ffascinating-star-trek-quotes-gallery-most-misquoted-line-014308748.html
And paste it into the URL Encoded box on http://www.asciitohex.com then click convert. The Text section at the top will now have:
s=75d28bf1d1cc1a104334494b15f1a20f&c=PRIVMSG #memory-alpha :Sheesh, I like this page more than I should. Bones’ quotes are especially great: http://movies.yahoo.com/blogs/movie-talk/fascinating-star-trek-quotes-gallery-most-misquoted-line-014308748.html
That URL will not be needed now, but we’ll take note of it for later.
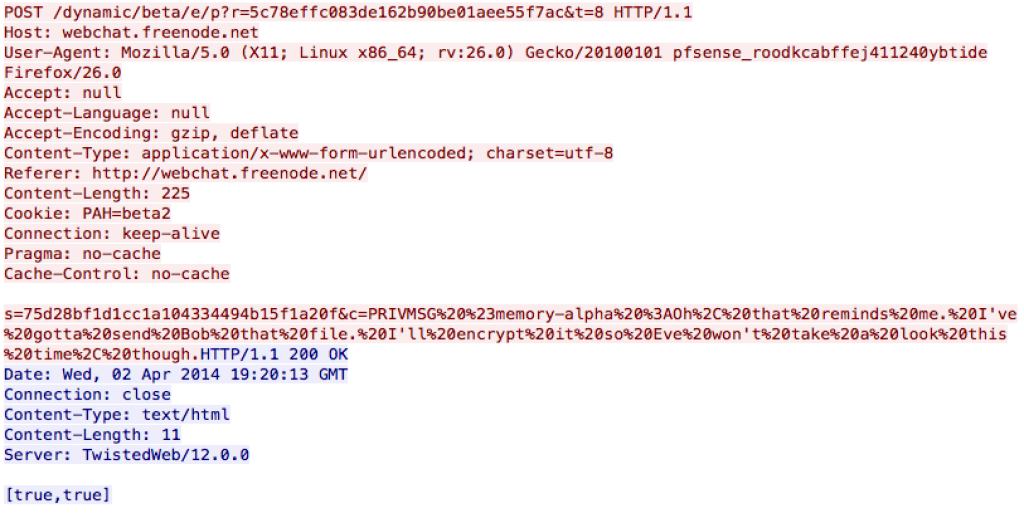
The filter “tcp.stream eq 28” has another interesting POST we can decode in the same way:
s=75d28bf1d1cc1a104334494b15f1a20f&c=PRIVMSG #memory-alpha :Oh, that reminds me. I’ve gotta send Bob that file. I’ll encrypt it so Eve won’t take a look this time, though.
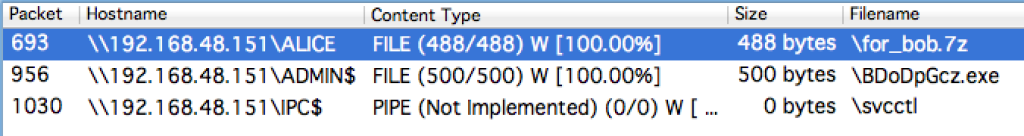
Then, tcp.stream eq 29 contains an SMB file transfer. By using “File | Export Objects | SMB/SMB2” in Wireshark, we can export “for_bob.7z”:
As indicated in the IRC message, this file is encrypted so we need the password.
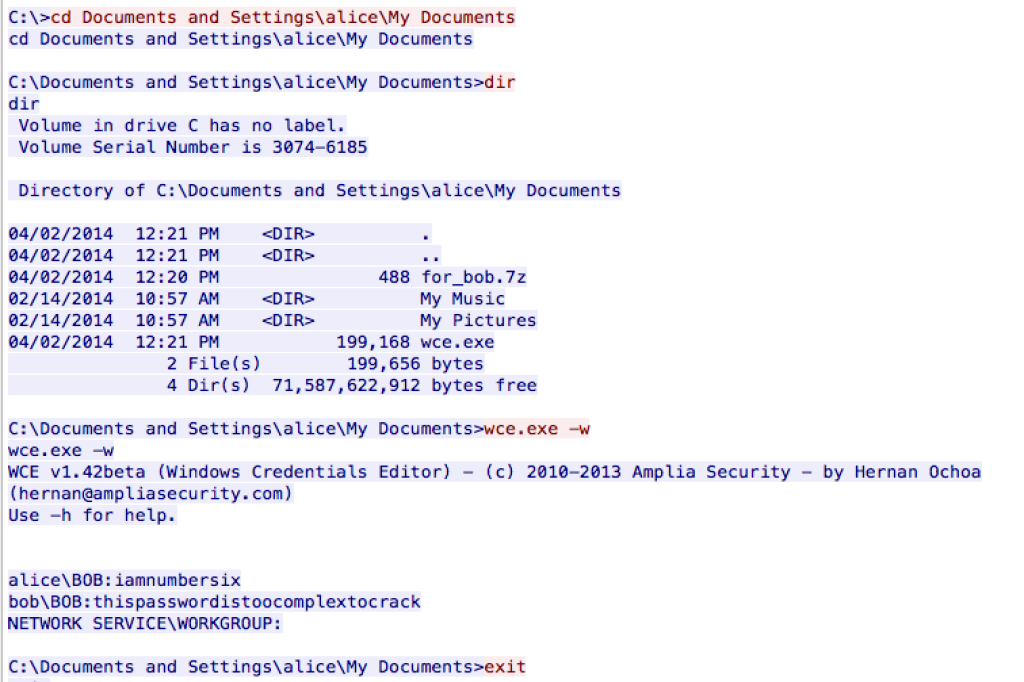
Using the filter “tcp.stream eq 35”, we see a short metasploit session:
Unfortunately, these passwords won’t unzip the for_bob.7z file, but again we can save this information for later. Instead, if we return to the Yahoo page containing the Star Trek quotes and look for ones by Bones, we’ll find that the password is “Space is disease and danger wrapped in darkness and silence.” (without the quotes).
Extracting the zip with that password reveals a supersecret.txt with the following:
Bob,
I’ve encrypted this message so Eve can’t intercept it. I can’t believe she’s *still* listening in on our conversations. We’ve been talking for what, thirty-five years? More?
Anyway, here’s the link I promised: http://bit.ly/1hhVjGP
– Alice
P.S.
As for our normal conversations, here’s my favorite cat video: http://www.youtube.com/watch?v=Of2HU3LGdbo
The bit.ly link goes to http://brochure2014.counterhack.com/Challenge-1-Level-3-B9157BE3-2D0E-4674-9483-4D23F194270E/ which has the text:
Congratulations, you’ve graduated from Starfleet Academy! Before you make Captain, though, you’ll need to solve other challenges to unlock the final piece of this puzzle.
Remember what comes first as you proceed, though: “Mister Donut Always Delivers Muffins”. Download here.
“Download here” is a link to http://brochure2014.counterhack.com/Challenge-1-Level-3-B9157BE3-2D0E-4674-9483-4D23F194270E/file1.
The hint reads “Mister Donut Always Delivers Muffins”. The first letter of each word makes an acronym MDADM and, with a simple search, we can determine it refers to mdadm, a Linux software RAID utility. We have file1 now, and we will need the other image files to complete the RAID. Each challenge will end with a different file, so we’ll have 4 files in total.
SANS Baltimore
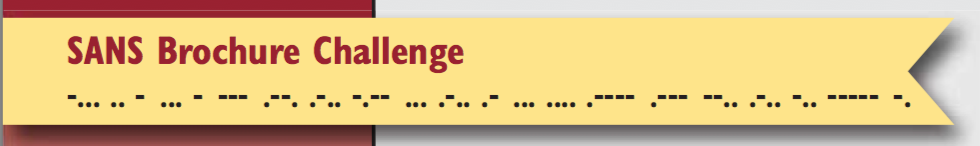
Page 7 of the PDF (page 5 on the brochure) has the brochure challenge banner in this issue with the following Morse Code:
This translates to
BITSTOPLYSLASH1JZLD0N
or
bit.ly/1JZLD0N
This redirects to http://brochure2014.counterhack.com/Challenge-2-Level-1-98ED8090-21D0-4C4D-BC23-4130CBC70878/.
Which has the following text:
The Force is strong with our family of SANS instructors. Extract the following intel from instructors’ presentations.
Be warned, though. Some of these items are as elusive as womp rats.
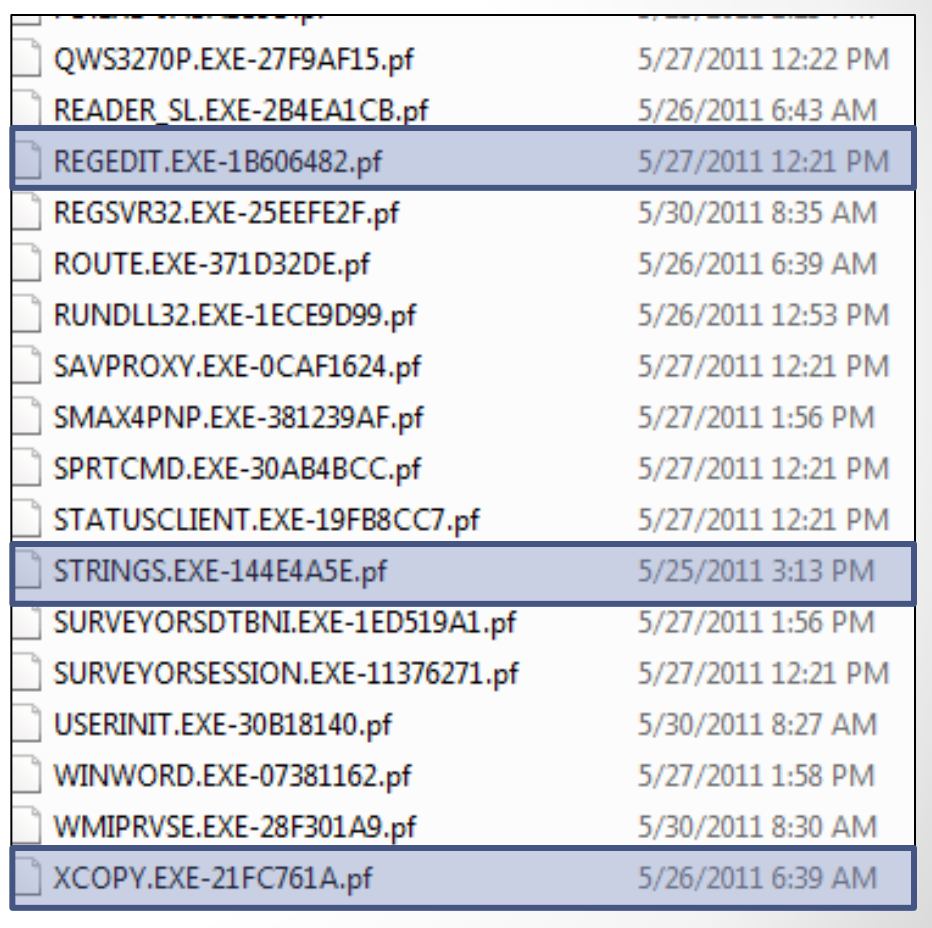
- Out of the three highlighted prefetch entries in Alissa Torres’ presentation from DFIR Summit 2012, what corresponding executable is not included in default Windows installations? (Answer in all lowercase)
- Examine the “Integrating Mobile and Network Attacks for In-Depth Pwnage” presentation by Ed Skoudis and Josh Wright. According to Alan Paller, what don’t we have enough of? (Answer in all lowercase)
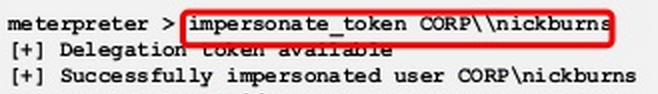
- What is the username whose token Bryce Galbraith impersonates in his Seattle 2013 presentation? (just the username, no domain)
Add the three answers to http://bit.ly/SANS_ (without spaces, all lowercase) in order to reveal the next challenge.
Alissa’s presentation is at http://digital-forensics.sans.org/summit-archives/2012/why-not-to-stay-in-your-lane-as-a-digital-forensic-examiner.pdf. Page 6 contains a list of prefetch files and the non-default Windows application is strings.exe.
Ed and Josh’s presentation is at https://blogs.sans.org/pen-testing/files/2014/01/561-webcast.pdf. Slide 24 contains the quote from Alan Paller with the answer being pilots.
Finally, Bryce’s presentation is at http://www.slideshare.net/brycegalbraith/why-are-our-defenses-failing-one-click-is-all-it-takes. Slide 31 shows a meterpreter session where he impersonates the token of nickburns.
This gives us bit.ly/SANS_stringspilotsnickburns and redirects to http://brochure2014.counterhack.com/Challenge-2-Level-2-96925C5F-B1F4-4940-B704-BC2E8CBC6800/.
Which has the following text:
Done well you have!
You’ve successfully decoded the encoded text and found this site. In the words of Count Dooku, though… this is just the beginning. Answer the below question and continue on, young Padawan.
Carol has used Firefox for Android to search for, browse, and save a particular image. A compressed copy of her /data/data/org.mozilla.firefox folder is downloadable here. What is the serial number of the lens used to take the downloaded picture? Add the full serial number to the end of http://bit.ly/SANS_ to progress forward.
Hint: You may have to use resources outside the org.mozilla.firefox folder to fully answer this question.
Unzipping the Firefox data from the download link, in org.mozilla.firefox/files/mozilla/9tnld04f.default, we can look at the history:
$ tar -zxf org.mozilla.firefox.tgz $ cd org.mozilla.firefox/files/mozilla/9tnld04f.default/ $ sqlite3 browser.db SQLite version 3.7.13 2012-07-17 17:46:21 Enter ".help" for instructions Enter SQL statements terminated with a ";" sqlite> select * from history; 1|harrison ford han solo comic con - Google Search|https://www.google.com/search?q=harrison+ford+han+solo+comic+con&ie=utf-8&oe=utf-8&aq=t&rls=org.mozilla:en-US:official|1|4|1392762220192|1392762220193|1392762220388|MD-yXAaFyT8n|0 2|harrison ford han solo comic con - Google Search|https://www.google.com/images?q=harrison+ford+han+solo+comic+con&oe=utf-8&rls=org.mozilla%3Aen-US%3Aofficial&hl=en&sa=X&oi=image_result_group&ei=bN0DU62oA9LaoATH24LgBg&ved=0CAsQsAQ|1||1392762223983|1392762223989|1392762224105|sSslhqzIDbYl|0 3|harrison ford han solo comic con - Google Search|https://www.google.com/images?q=harrison+ford+han+solo+comic+con&oe=utf-8&rls=org.mozilla%3Aen-US%3Aofficial&hl=en&sa=X&oi=image_result_group&ei=bN0DU62oA9LaoATH24LgBg&ved=0CAsQsAQ#|1||1392762224970|1392762224971|1392762224996|VPqjDulKQtRk|0 4|harrison ford han solo comic con - Google Search|https://www.google.com/images?q=harrison+ford+han+solo+comic+con&rls=org.mozilla:en-US:official&hl=en&tbm=isch&ei=b90DU4rZLdfloASKvIGYCQ&start=20&sa=N|1||1392762232161|1392762232163|1392762232252|0NJPgjqylSKg|0 5|harrison ford han solo comic con - Google Search|https://www.google.com/images?q=harrison+ford+han+solo+comic+con&rls=org.mozilla:en-US:official&hl=en&tbm=isch&ei=b90DU4rZLdfloASKvIGYCQ&start=20&sa=N#|1||1392762232803|1392762232804|1392762232814|T4thX7ACWW_o|0 6|harrison ford han solo comic con - Google Search|https://www.google.com/images?q=harrison+ford+han+solo+comic+con&rls=org.mozilla:en-US:official&hl=en&tbm=isch&ei=b90DU4rZLdfloASKvIGYCQ&start=20&sa=N#i=8|1||1392762236646|1392762236651|1392762236659|mJ_g8jlQDXq2|0 7|173974131.jpg (JPEG Image, 1000 × 758 pixels)|http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000|1|5|1392762243050|1392762243051|1392762243541|BHlaG0nvvlzS|0
This shows a Google search for “harrison ford han solo comic con” and, finally in row 7, downloading an image 173974131.jpg from a wordpress site.
$ sqlite3 downloads.sqlite SQLite version 3.7.13 2012-07-17 17:46:21 Enter ".help" for instructions Enter SQL statements terminated with a ";" sqlite> select * from moz_downloads; 1|173974131.jpg|http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000|file:///storage/emulated/0/Download/173974131.jpg||1392762252466744|1392762252537026|1|http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000||333764|333764|||0|0|abwrZ5us7Wr2
The download history indicates a JPG file was downloaded, so we should be able to find it in the Firefox cache. From org.mozilla.firefox/files/mozilla/9tnld04f.default/Cache, run this:
$ find . -type f -exec file {} \; | grep JPEG
./0/0A/52437d01: JPEG image data, JFIF standard 1.01
Now we can run exiftool on that file, but there is no information on the lens.
$ exiftool 0/0A/52437d01 | grep Lens
Instead, download the file from http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000
Then, run exiftool:
$ exiftool 173974131.jpg | grep Lens Lens Info : 70-200mm f/0 Lens Model : EF70-200mm f/2.8L IS II USM Lens Serial Number : 0000c15998
This gives us the URL http://bit.ly/SANS_0000c15998 which redirects to http://brochure2014.counterhack.com/Challenge-2-Level-3-63A2BD6A-0A72-4F84-9949-587E7AB7254A/ and has the following text:
Do you remember that scene from Episode IV, where Luke and Han get Medals of Bravery from Princess Leia? Well, you deserve one too!
Unfortunately, just like Chewbacca, you’re not going to get one. You can download this file, though, along with some others, to get your own reward!
P.S. No, the comic book doesn’t count. You’re really not getting a Medal of Bravery. Sorry ’bout that!
The link is for file2, the second file in the mdadm RAID, and this ends the challenge for this brochure.
SANS Seattle
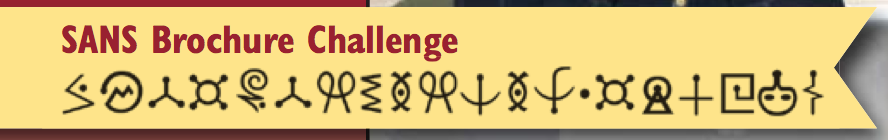
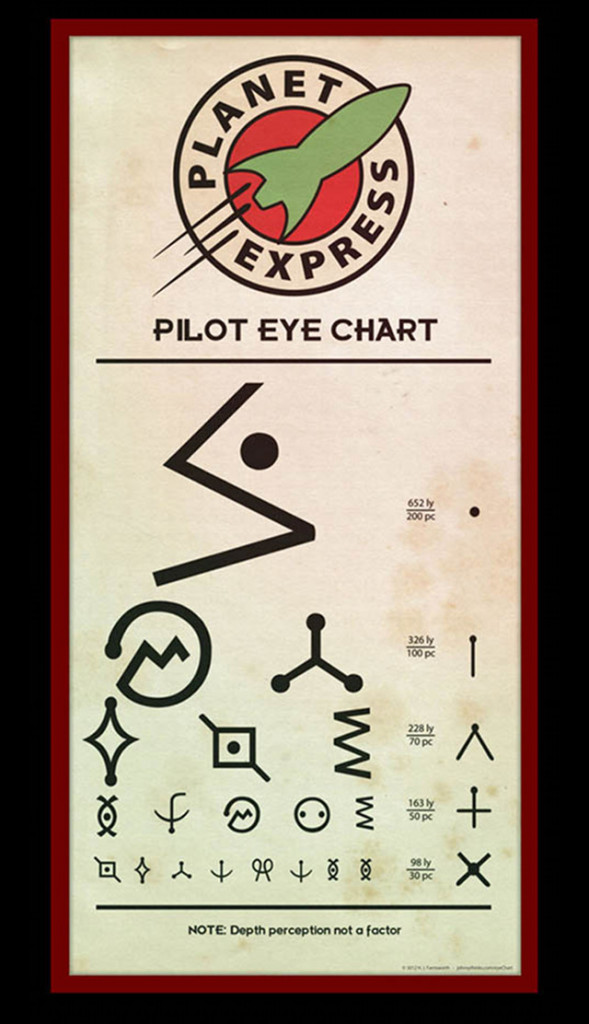
Page 6 of the PDF (page 4 on the brochure) has the brochure challenge banner in this issue with the following symbols:
I cut out one of the images:
Then searched at Google’s Search by Image at http://www.google.com/insidesearch/features/images/searchbyimage.html, which revealed some images related to Futurama:
In particular, I found the Pilot Eye Chart in the results.
These symbols are part of the Futurama alien language. This page on Alienese shows an image mapping letters to the symbols:
http://futurama.wikia.com/wiki/Alienese
Mapping the letters from the brochure gives BITDOTLYSLASH1DR4FZG or bit.ly/1DR4FZG which redirects to http://brochure2014.counterhack.com/Challenge-3-Level-1-6A20856D-F322-4CA7-95AC-66FEC65A2546/ and has the following text:
Good news, everyone!
You weren’t fooled by Alienese, were you? Well, before you can become the most important person in the universe, you have some more challenges to finish.
- What is the last name of the winner of the second annual NetWars Tournament of Champions?
- What is the only tool to be listed on both the “Mobile Device” and “Web App” sections of the SANS Ultimate Pen Test Poster?
- How many cans of Red Bull are visible in Dr. Cole’s champagne bucket picture from #SANSScottdale 2014? Be sure to spell out the number (i.e., use “Six” instead of “6”).
Add the three answers to http://bit.ly/SANS_ (without spaces, but keeping the original capitalization) in order to reveal the next section.
The last name of the winner of NetWars can be found at
https://www.sans.org/press/sans-announces-winner-second-annual-netwars-tournament-of-champions.php. His name is Matthew Toussain (0sm0s1z).
The poster can be found at http://pen-testing.sans.org/blog/pen-testing/2013/06/20/announcing-the-ultimate-sans-pen-test-poster. The only tool listed in both “Mobile Device” and “Web App” sections of the poster is Burp Suite.
Dr. Cole’s twitter image can be found at https://twitter.com/drericcole/status/436515767152947200/photo/1. There are Four Red Bull cans visible.
Combining these answers gives us https://bit.ly/SANS_ToussainBurpSuiteFour which redirects to http://brochure2014.counterhack.com/Challenge-3-Level-2-46EE0A03-B770-4B4A-B69A-2651DB1E1BF9/ and has the following text:
Obligatory Zapp Brannigan quote: “If you can hit the bulls-eye, the rest of the dominoes will fall like a house of cards. Checkmate.”
Dave messed up a tar command and deleted a WAV file on accident. He’d really appreciate it if you could retrieve it for him – here’s a download that might help.
Once you’ve recovered the audio file, look at it carefully to find the next URL.
The link is http://brochure2014.counterhack.com/Challenge-3-Level-2-46EE0A03-B770-4B4A-B69A-2651DB1E1BF9/repo.svn_dump.gz. Download the file and gunzip it. The file appears to be an SVN repo. I tried restoring the repo, but I don’t have much SVN experience and kept getting errors. After getting frustrated with that for a while, I just decided to locate the file manually and dump it.
First, I looked at what files were in the repo:
$ grep -a Node-path repo.svn_dump Node-path: .bash_logout Node-path: .bashrc Node-path: .profile Node-path: examples.desktop Node-path: dontopen.mp3 Node-path: dontopen.mp3 Node-path: goals.txt
There wasn’t a WAV file, but there was an MP3, so I assumed that was the target. There’s some useful information around the two instances of “dontopen.mp3” in the repo:
$ grep -a dontopen -C 5 repo.svn_dump svn:log V 21 Added additional file PROPS-END Node-path: dontopen.mp3 Node-kind: file Node-action: add Prop-content-length: 59 Text-content-length: 492355 Text-content-md5: 33fa9536b5174d00005850332f8ec8d3 -- -- svn:log V 70 Oops! Cleared a file that shouldn't have been there in the first place PROPS-END Node-path: dontopen.mp3 Node-action: delete Revision-number: 4 Prop-content-length: 114
We see a message that the file was deleted and shouldn’t have been there. We also have the length of the target file and its MD5 which will help with extracting and verifying it. We just need to know the starting position of the file data. The grep matches above are in a properties section for the file. The full content of the properties section is:
Node-path: dontopen.mp3 Node-kind: file Node-action: add Prop-content-length: 59 Text-content-length: 492355 Text-content-md5: 33fa9536b5174d00005850332f8ec8d3 Text-content-sha1: fea00644b3454ee685c91be450183f5ccb5d7406 Content-length: 492414 K 13 svn:mime-type V 24 application/octet-stream PROPS-END ÿûÐÄ^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@Info^@^@^@^O^@^@^BL^@^G<83>C^@^B^E^G
We can see the properties ends with a PROPS-END and is immediately followed by the file data, so we just need the offset immediately following PROPS_END.
$ xxd repo.svn_dump | grep -C 3 END ...snip... -- 0003be0: 0a0a 4b20 3133 0a73 766e 3a6d 696d 652d ..K 13.svn:mime- 0003bf0: 7479 7065 0a56 2032 340a 6170 706c 6963 type.V 24.applic 0003c00: 6174 696f 6e2f 6f63 7465 742d 7374 7265 ation/octet-stre 0003c10: 616d 0a50 524f 5053 2d45 4e44 0aff fbd0 am.PROPS-END.... 0003c20: c400 0000 0000 0000 0000 0000 0000 0000 ................ 0003c30: 0000 496e 666f 0000 000f 0000 024c 0007 ..Info.......L.. 0003c40: 8343 0002 0507 0a0d 0f12 1417 1a1c 1f21 .C.............! -- ...snip...
This hexdump and grep shows the PROPS-END preceded by “application/octet-stream” and followed by binary data, so this looks like the right offset. PROPS-END is followed by hex character 0x0A, which is the newline character, so the start of the data we want is the 0xFF at offset 0x3C1D, or decimal 15389.
Extract the mp3 with:
$ dd if=repo.svn_dump skip=15389 bs=1 count=492355 of=dontopen.mp3 $ md5 dontopen.mp3 MD5 (dontopen.mp3) = 33fa9536b5174d00005850332f8ec8d3
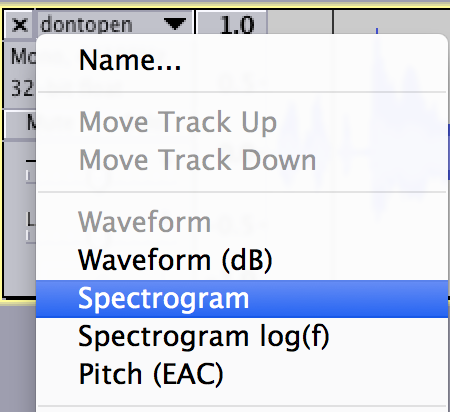
The MD5 of the extracted file matches the MD5 is the properties data from the SVN repo, so it looks like we have the right file. Open in Audacity and select the Spectrogram.
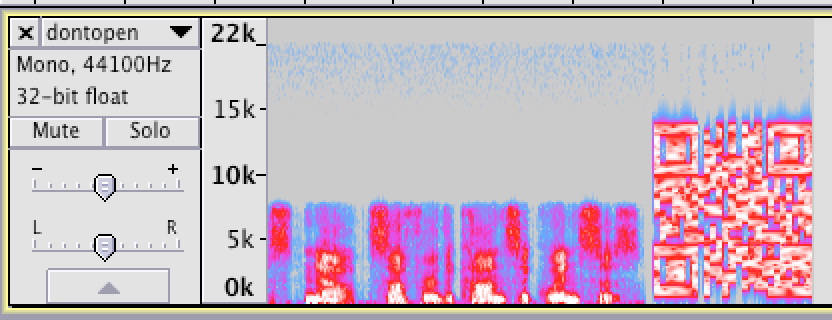
Scroll to the right and we see what looks like a QR code.
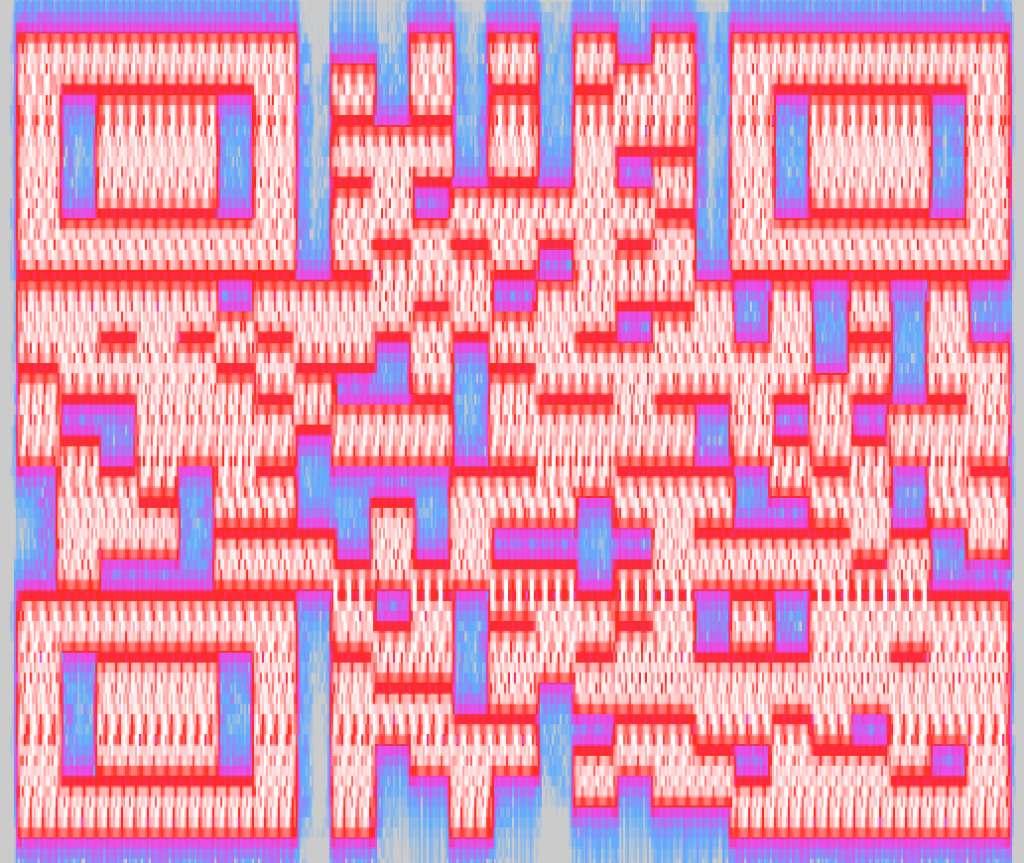
I tried scanning this with a QR code reader, but it wouldn’t work, so I rebuilt the QR code in Excel. After zooming in on the spectrogram, it took a few minutes, but it wasn’t too hard to figure out what needed to be black vs. white.
Scanning the Excel image with a QR code reader opens http://bit.ly/1lmqWnz which redirects to
http://brochure2014.counterhack.com/Challenge-3-Level-3-70A90642-FFBF-476B-83DD-48DE266C9B51/ which has the following text:
Did you go back in time and give yourself the answer? Well, either way, great work!
Download the following file and use it, along with others, to reveal the final answer.
This will download file3, the third of the 4 files we need, and ends the challenge for this brochure.
SANS Network Security
Page 6 of the PDF (page 2 on the brochure) introduces the brochure challenge. For this brochure, the challenge is to find all the diamond shapes with a number in them and assemble them. The shapes look like this:

Finding all the images will give you the following (PDF page numbers, subtract 4 to get the printed page number):
- 98 – page 6
- 105 – page 9
- 116 – page 12
- 46 – page 19
- 108 – page 25
- 121 – page 33
- 47 – page 35
- 80 – page 40
- 55 – page 46
- 77 – page 49
- 108 – page 61
- 70 – page 65
- 70 – page 82
These look like decimal values of ASCII so if we convert each number to its corresponding letter (98=b, 105=i, etc.) we get bit.ly/P7MlFF. This redirects to http://brochure2014.counterhack.com/Challenge-4-Level-1-756D0EF9-2285-4D68-BFE4-C24BE0A003BD/.
This page has the following text:
Good work, recruit. Welcome aboard the Battlestar Galactica. Your next mission is to prove your knowledge of SANS lore.
- What software did John Strand run during a recorded call with online scammers to scare and confuse them?
- What software does Lenny Zeltser have a YouTube video of running in order to create a memory capture?
Add the two answers to http://bit.ly/SANS_ (without spaces, with the original capitalization) in order to reveal the next section.
Turning to Google we can find the answers to these questions:
- The video of John Strand is at https://www.youtube.com/watch?v=6ftRs73dx4s. In the video, he uses Poison Ivy.
- The video from Lenny Zeltser is at https://www.youtube.com/watch?v=SEs4ZAolED0. In the video, he uses DumpIt.
These two answers give us the next link: http://bit.ly/SANS_PoisonIvyDumpIt which redirects to http://brochure2014.counterhack.com/Challenge-4-Level-2-6936232A-C867-4CFD-9893-36923470871B/
This page has the following text:
Congratulations! You’ve done very well.
Yes, you’re tired. Yes, there is no relief. Yes, the questions keep coming after you time after time after time. And yes, you are still expected to persist!
Eve suspects that one of the other characters might not be as innocent as they claim to be. She’ll need your help to prove it, however. Examine the other three questions from Level 2 and the included files. Which user, based off their malicious behavior, might be a Cylon?
Once you know who it is, find their password and add it to the end of http://bit.ly/SANS_232E28B95F01_ to continue this quest.
So say we all!
From the PCAP in the Albuquerque challenge, the metasploit session did prove helpful with the password for alice\BOB, which was iamnumbersix. Putting this into the link gives http://bit.ly/SANS_232E28B95F01_iamnumbersix, which redirects to http://brochure2014.counterhack.com/Challenge-4-Level-3-E071FCF5-1876-462B-BC0F-1C6648DB41D4/ and has the following text:
You’ve uncovered the Cylon and completed this part of the challenge. Before your promotion, though, you’ll need to answer other questions.
Download the below file, in combination with other parts, to complete the entire challenge.
“Download here” links to the final file, file4, and is the end of this challenge. The link of the word “file” is to the Linux man page for the file command. Running this on the 4 downloaded files seemed like it might have been a hint, but I didn’t get any additional information:
$ file file* file1: data file2: data file3: data file4: data
Putting It All Together
The file command didn’t help with identifying the files, but the original hint to use mdadm proves to be correct. We can run the following commands to setup and mount the software RAID with mdadm. The first four commands create loopback devices for the 4 separate files. The mdadm command combines the 4 devices into a single device. Finally, the mount command mounts the device at the mountpoint /mnt.
$ sudo losetup /dev/loop0 file1 $ sudo losetup /dev/loop1 file2 $ sudo losetup /dev/loop2 file3 $ sudo losetup /dev/loop3 file4 $ sudo mdadm --assemble /dev/md0 /dev/loop0 /dev/loop1 /dev/loop2 /dev/loop3 mdadm: /dev/md0 has been started with 4 drives. $ sudo mount /dev/md0 /mnt $ ls /mnt lost+found README.txt winner.7z
Looking in /mnt, we can see a README.txt file:
Congratulations, dear challenger. You have proven your knowledge of encodings, SANS lore, technology, and assorted geekery.
The passphrase for the encrypted 7-zip file is: “How about a nice game of chess?”
The other file in /mnt is the referenced winner.7z. Using that password on winner.7z extracts a few bonus pictures, a file called randombits to make sure the 7z file was big enough to span all the device files, and a final text file “how to win.txt”.
$ 7za x -p"How about a nice game of chess?" winner.7z 7-Zip (A) [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 p7zip Version 9.20 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,1 CPU) Processing archive: winner.7z Extracting winning/randombits Extracting winning/bonus_pictures/Battlestar Galactica.jpg Extracting winning/bonus_pictures/Firefly.jpg Extracting winning/bonus_pictures/President Bush and Internet Storm Center.jpg Extracting winning/bonus_pictures/SANS instructors on stage.jpg Extracting winning/bonus_pictures/SANS trio.jpg Extracting winning/bonus_pictures/Futurama.png Extracting winning/how to win.txt Extracting winning/bonus_pictures Extracting winning Everything is Ok Folders: 2 Files: 8 Size: 11938981 Compressed: 12021769
The contents of “how to win.txt” are as follows:
Congratulations! You’ve bested all of our challenges… save one.
Send an email to jeff@counterhack.com with the subject line “Brochure Challenge – The Beauty of the Baud”. In the body of the email, include a brief explanation of the steps you took to solve the main technical challenges (Alice’s encrypted file for Bob, Carol’s Firefox for Android, Dave’s recovered WAV file, and the Cylon question). One paragraph each is sufficient.
I sent Jeff an email and got a response back that I was done. Again, it was a great challenge, and I look forward to the next one.